Safety researcher Bobby Gould has revealed a weblog submit demonstrating an entire exploit chain for CVE-2025-20281, an unauthenticated distant code execution vulnerability in Cisco Identification Companies Engine (ISE).
The important vulnerability was first disclosed on June 25, 2025, with Cisco warning that it impacts ISE and ISE-PIC variations 3.3 and three.4, permitting unauthenticated, distant attackers to add arbitrary information to the goal system and execute them with root privileges.
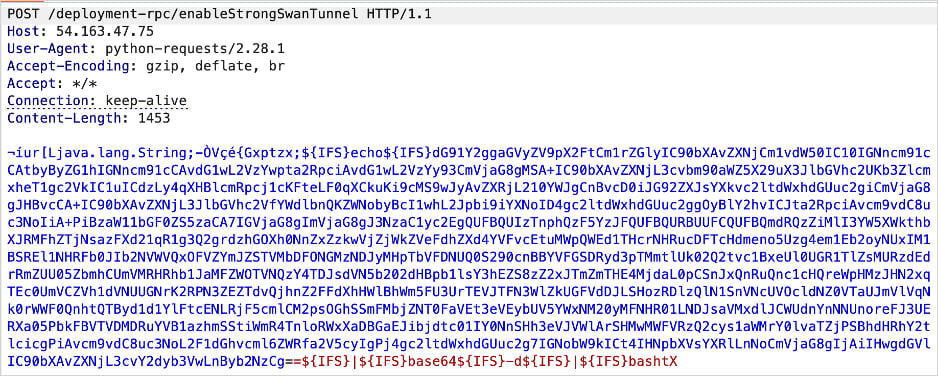
The difficulty stems from unsafe deserialization and command injection within the enableStrongSwanTunnel() methodology.
Three weeks later, the seller added yet another flaw to the identical bulletin, CVE-2025-20337, which pertains to the identical flaw however is now damaged down into two components, CVE-2025-20281 (command injection) and CVE-2025-20337 (deserialization).
Though hotfixes had been beforehand made out there, Cisco urged customers to replace to three.3 Patch 7 and three.4 Patch 2 to deal with each vulnerabilities.
On July 22, 2025, Cisco marked each CVE-2025-20281 and CVE-2025-20337 as actively exploited in assaults, urging admins to use the security updates as quickly as doable.
With adequate time having handed, permitting directors to use the updates, Gould has now revealed his write-up, the place he demonstrates triggering the command injection flaw in Cisco ISE through a serialized Java String[] payload.
The researcher achieves arbitrary command execution as root inside a Docker container by exploiting the habits of Java’s Runtime.exec() and utilizing ${IFS} to bypass argument tokenization points.
Lastly, Gould demonstrates learn how to escape from the privileged Docker container and acquire root entry on the host system utilizing a well known Linux container escape approach primarily based on cgroups and release_agent.
Supply: zerodayinitiative.com
Though Gould’s write-up is not a weaponized exploit script hackers can instantly plug into their assault chain, it supplies all of the technical particulars and payload construction crucial for expert hackers to recreate the entire exploit.
Even when energetic exploitation within the wild is already underway, the discharge of this exploit is certain to extend malicious exercise.
There are not any workarounds for this vulnerability, so making use of the patches as directed within the vendor’s bulletin is the really helpful plan of action.

CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud security drives enterprise worth.
This free, editable board report deck helps security leaders current threat, affect, and priorities in clear enterprise phrases. Flip security updates into significant conversations and quicker decision-making within the boardroom.




