Researchers have launched proof-of-concept (PoC) exploits for a crucial Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the flaw is well exploitable and may efficiently steal person session tokens.
The CitrixBleed 2 vulnerability, which impacts Citrix NetScaler ADC and Gateway units, permits attackers to retrieve reminiscence contents just by sending malformed POST requests throughout login makes an attempt.
This crucial flaw is called CitrixBleed2 because it intently resembles the unique CitrixBleed (CVE-2023-4966) bug from 2023, which was exploited by ransomware gangs and in assaults on governments to hijack person periods and breach networks.
In technical analyses first launched by watchTowr after which Horizon3, researchers confirmed that the vulnerability might be exploited by sending an incorrect login request, the place the login= parameter is modified so it is despatched with out an equal signal or worth.
This causes the NetScaler equipment to show the reminiscence contents as much as the primary null character within the <InitialValue></InitialValue> part of the response, as proven under.
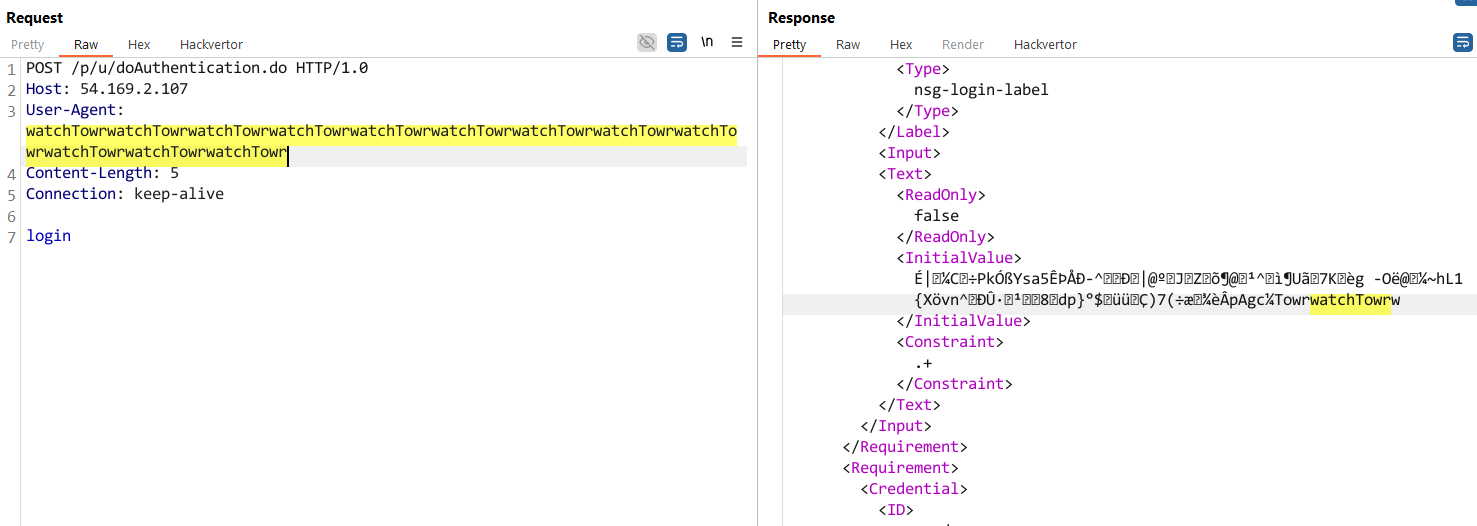
Supply: WatchTowr
The flaw is triggered by means of the snprintf perform together with a format string containing the %.*s format string.
“The %.*s format tells snprintf: “Print as much as N characters, or cease on the first null byte (�) – whichever comes first.” That null byte finally seems someplace in reminiscence, so whereas the leak doesn’t run indefinitely, you continue to get a handful of bytes with every invocation,” explains watchTowr’s report.
“So, each time you hit that endpoint with out the =, you pull extra uninitialized stack knowledge into the response.”
In accordance with Horizon3, every request leaks roughly 127 bytes of knowledge from knowledge, permitting attackers to carry out repeated HTTP requests to extract further reminiscence contents till they discover the delicate knowledge they’re in search of.
Whereas the makes an attempt by WatchTowr had been unsuccessful, Horizon3 demonstrates within the video under that they might exploit this flaw to steal person session tokens.
Along with NetScaler endpoints, Horizon3 states that the flaw may also be exploited towards configuration utilities utilized by directors.
Exploited or not?
Citrix continues to state that the flaw shouldn’t be actively being exploited, and when BleepingComputer beforehand inquired about its standing, the corporate referred us to a weblog submit in regards to the vulnerability.
“At the moment, there isn’t a proof to counsel exploitation of CVE-2025-5777,” reads the weblog submit.
Nevertheless, a June report by cybersecurity agency ReliaQuest signifies that there’s proof that CVE-2025-5777 might have been exploited in assaults, with the corporate seeing a rise in person session hijacks.
Moreover, security researcher Kevin Beaumont disputes Citrix’s assertion, saying the vulnerability has been actively exploited since mid-June, with attackers leveraging the bug to dump reminiscence and hijack periods.
He highlighted the next indicators of compromise:
- In Netscaler logs, repeated POST requests to *doAuthentication* – each yields 126 bytes of RAM
- In Netscaler logs, requests to doAuthentication.do with “Content material-Size: 5”
- In Netscaler person logs, traces with *LOGOFF* and person = “*#*” (i.e. # image within the username). RAM is performed into the fallacious subject.
“Price noting I used to be solely capable of finding exploitation exercise as a result of WatchTowr and Horizon3 write ups,” warned Beaumont.
“Citrix help would not disclose any IOCs and incorrectly claimed (once more — occurred with CitrixBleed) that no exploitation [was] within the wild. Citrix have gotta get higher at this, they’re harming clients.”
Citrix has launched patches to handle CVE-2025-5777, and all organizations are strongly urged to use them instantly now that public exploits can be found.
Whereas Citrix recommends terminating all lively ICA and PCoIP periods, directors ought to first overview present periods for any suspicious exercise earlier than doing so.

Whereas cloud assaults could also be rising extra subtle, attackers nonetheless succeed with surprisingly easy methods.
Drawing from Wiz’s detections throughout 1000’s of organizations, this report reveals 8 key methods utilized by cloud-fluent risk actors.




