CrushFTP warned clients of an unauthenticated HTTP(S) port entry vulnerability and urged them to patch their servers instantly.
As the corporate additionally defined in an e mail despatched to clients on Friday (seen by BleepingComputer), the security flaw allows attackers to realize unauthenticated entry to unpatched servers if they’re uncovered on the Web over HTTP(S).
“Please take speedy motion to patch ASAP. A vulnerability has been addressed immediately (March twenty first, 2025). All CrushFTP v11 variations had been affected. (No earlier variations are affected.) A CVE will likely be generated quickly,” the corporate warned.
“The underside line of this vulnerability is that an uncovered HTTP(S) port may result in unauthenticated entry. The vulnerability is mitigated If in case you have the DMZ characteristic of CrushFTP in place.”
Whereas the e-mail says this vulnerability solely impacts CrushFTP v11 variations, an advisory issued on the identical day says that each CrushFTP v10 and v11 are impacted, as cybersecurity firm Rapid7 first famous.
As a workaround, those that cannot instantly replace CrushFTP v11.3.1+ (which fixes the flaw) can allow the DMZ (demilitarized zone) perimeter community choice to guard their CrushFTP occasion till security updates may be deployed.
In response to Shodan, over 3,400 CrushFTP situations have their net interface uncovered on-line to assaults, though BleepingComputer could not decide what number of have already been patched.
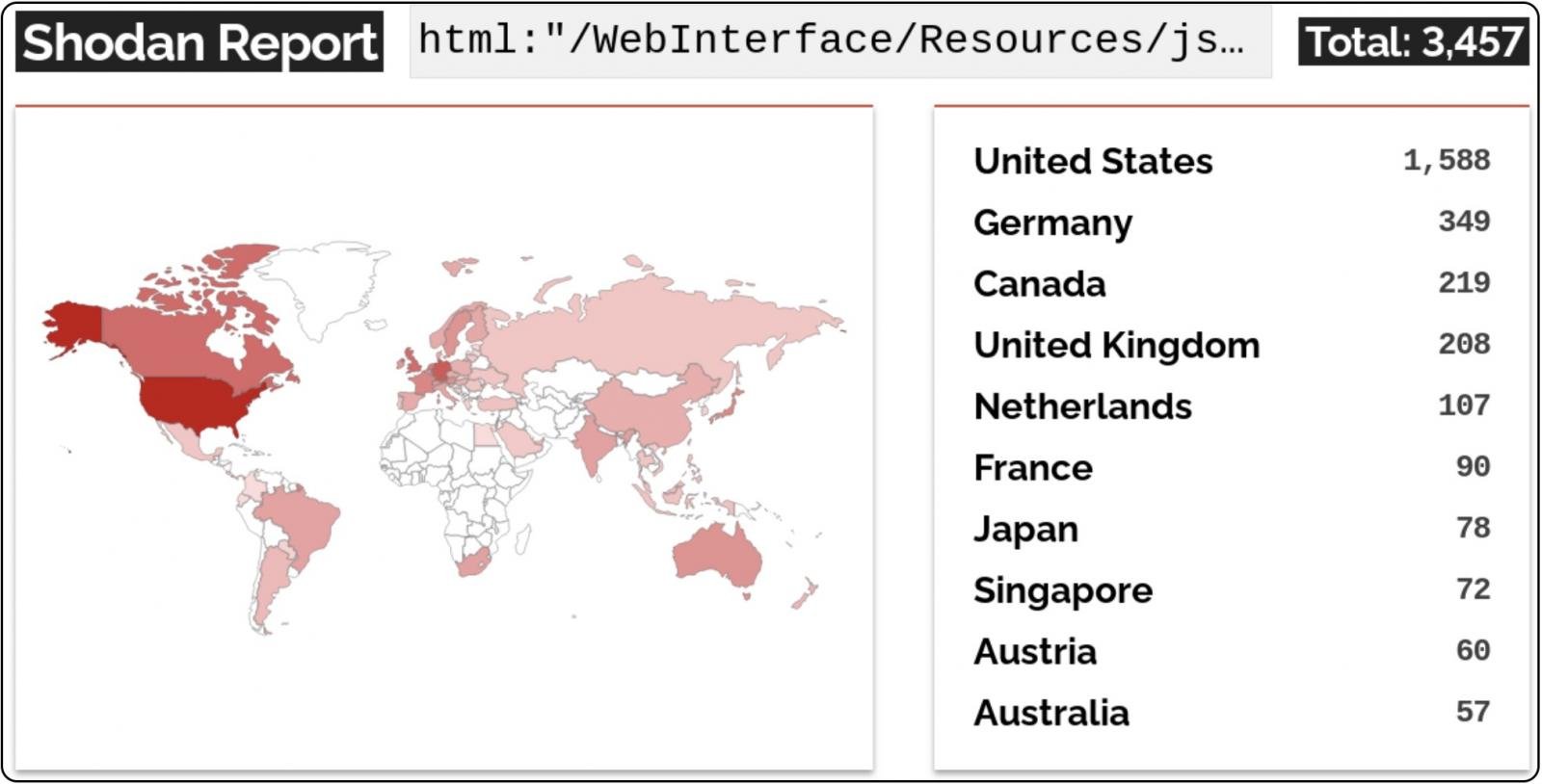
In April 2024, CrushFTP additionally launched security updates to patch an actively exploited zero-day vulnerability (CVE-2024-4040) that allowed unauthenticated attackers to flee the consumer’s digital file system (VFS) and obtain system recordsdata.
On the time, cybersecurity firm CrowdStrike discovered proof pointing to an intelligence-gathering marketing campaign, possible politically motivated, with the attackers focusing on CrushFTP servers at a number of U.S. organizations.
CISA added CVE-2024-4040 to its Identified Exploited Vulnerabilities catalog, ordering U.S. federal businesses to safe susceptible servers on their networks inside every week.
In November 2023, CrushFTP clients had been additionally warned to patch a important distant code execution vulnerability (CVE-2023-43177) within the firm’s enterprise suite after Converge security researchers who reported the flaw launched a proof-of-concept exploit three months after the flaw was addressed.
File switch merchandise like CrushFTP are engaging targets for ransomware gangs, particularly Clop, which was linked to knowledge theft assaults focusing on zero-day vulnerabilities in MOVEit Switch, GoAnywhere MFT, Accelion FTA, and Cleo software program.

Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and how you can defend towards them.




