A crucial vulnerability affecting a number of variations of GitHub Enterprise Server could possibly be exploited to bypass authentication and allow an attacker to realize administrator privileges on the machine.
The security problem is recognized as CVE-2024-6800 and obtained a 9.5 severity ranking as per the CVSS 4.0 commonplace. It’s described as an XML signature wrapping downside that happens when utilizing the Safety Assertion Markup Language (SAML) authentication commonplace with sure id suppliers.
GitHub Enterprise Server (GHES) is an area model of GitHub for companies that lack the expertise for working with the general public cloud or wish to handle entry and security controls.
In line with the FOFA search engine for community property uncovered on the general public net, there are greater than 36,500 GHES cases accessible over the web, most of them (29,200) positioned in the USA.
Nonetheless, it’s unclear how most of the uncovered GHES machines are operating a susceptible model of the product.
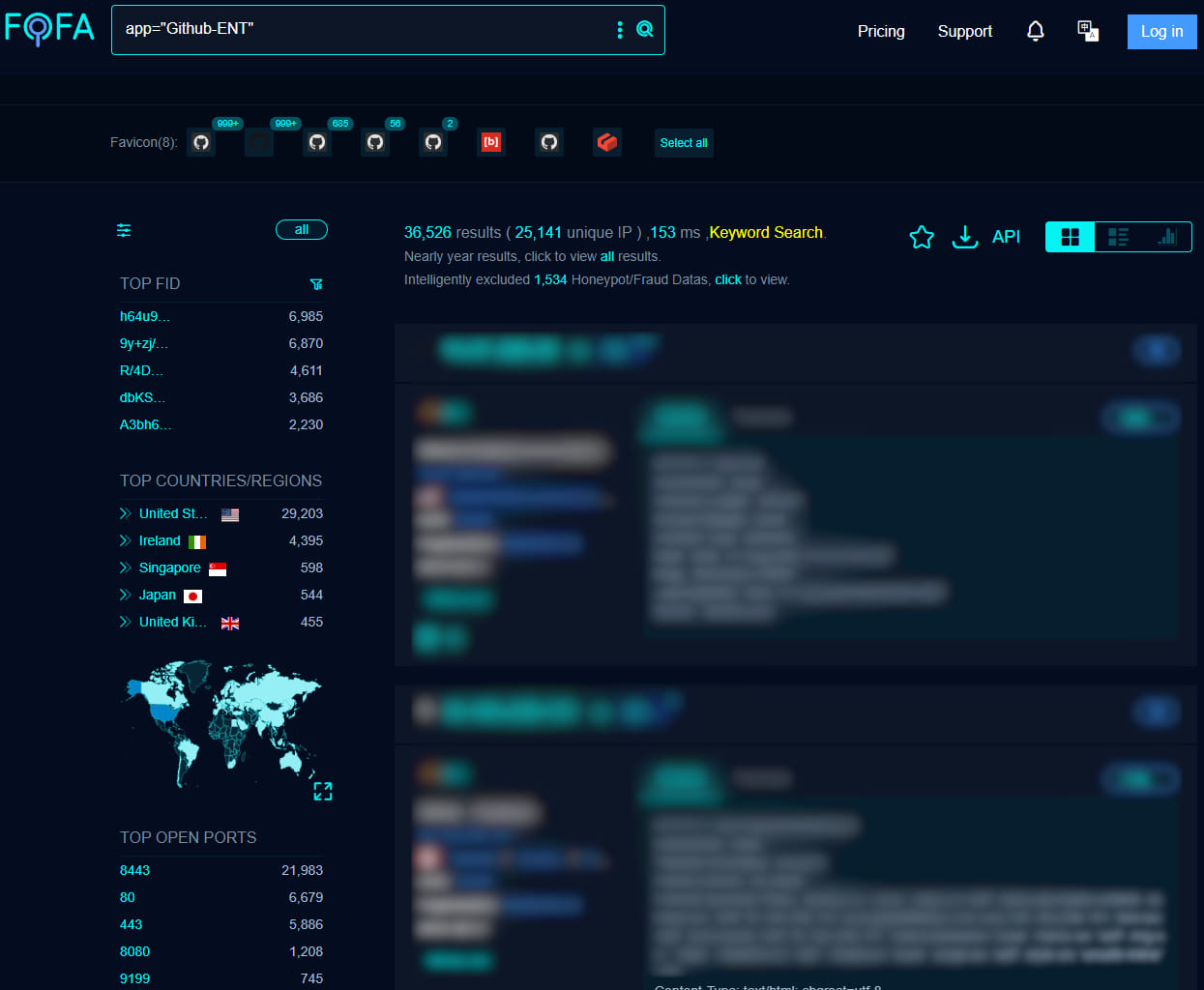
Supply: BleepingComputer
GitHub has addressed the problem in GHES variations 3.13.3, 3.12.8, 3.11.14, and three.10.16.
The brand new GHES releases additionally embody fixes for 2 different vulnerabilities, each with a medium severity rating:
- CVE-2024-7711: permits points on public repositories to be modified by attackers
- CVE-2024-6337: pertains to disclosing problem content material from a non-public repository
All three security points have been reported by GitHub’s Bug Bounty program on the HackerOne platform.
GitHub warns that some providers would possibly present errors through the configuration course of after making use of the security updates however occasion ought to nonetheless begin appropriately.
A number of points associated to log entries, reminiscence utilization, and repair interruptions throughout particular operations are additionally famous within the bulletin, so system admins are suggested to test the ‘Recognized points’ part earlier than they apply the replace.




