Citrix notified prospects this week to manually mitigate a PuTTY SSH consumer vulnerability that might enable attackers to steal a XenCenter admin’s personal SSH key.
XenCenter helps handle Citrix Hypervisor environments from a Home windows desktop, together with deploying and monitoring digital machines.
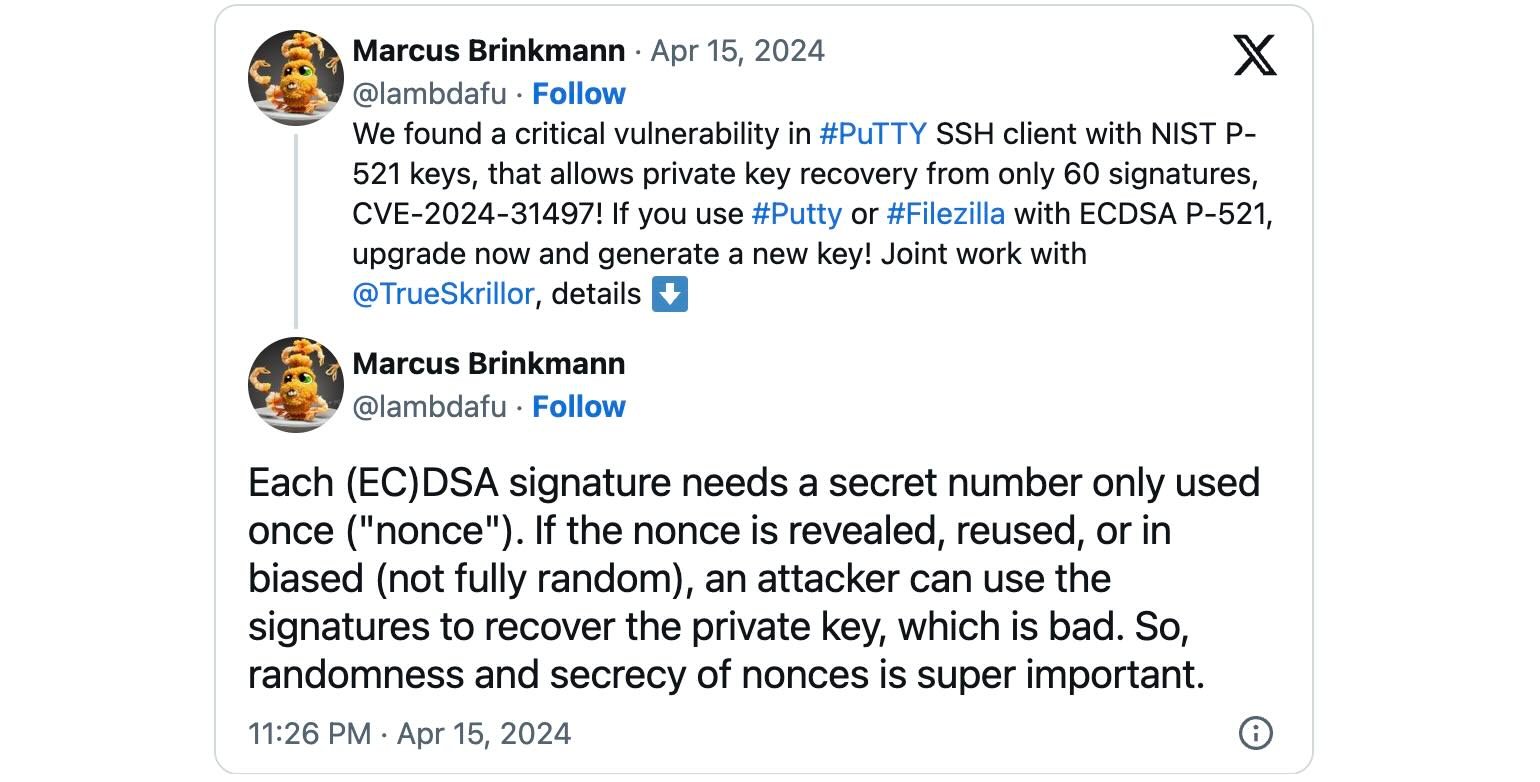
The security flaw (tracked as CVE-2024-31497) impacts a number of variations of XenCenter for Citrix Hypervisor 8.2 CU1 LTSR, which bundle and use PuTTY to make SSH connections from XenCenter to visitor VMs when clicking the “Open SSH Console” button.
Citrix says that the PuTTY third-party part has been eliminated beginning with XenCenter 8.2.6, and any variations after 8.2.7 will now not embrace it.
“A problem has been reported in variations of PuTTY previous to model 0.81; when used along with XenCenter, this subject could, in some situations, enable an attacker who controls a visitor VM to find out the SSH personal key of a XenCenter administrator who makes use of that key to authenticate to that visitor VM whereas utilizing an SSH connection,” Citrix explains in a Wednesday security advisory.
Discovered and reported by Fabian Bäumer and Marcus Brinkmann of Ruhr College Bochum, CVE-2024-31497 is brought on by how older variations of the Home windows-based PuTTY SSH consumer generate ECDSA nonces (momentary distinctive cryptographic numbers) for the NIST P-521 curve used for authentication.
The corporate advised admins who wish to mitigate the vulnerability to obtain the newest model of PuTTY and set up it instead of the model bundled with older XenCenter releases.
“Clients who don’t want to use the “Open SSH Console” performance could take away the PuTTY part utterly,” Citrix added.
“Clients who want to preserve the present utilization of PuTTY ought to change the model put in on their XenCenter system with an up to date model (with a model variety of not less than 0.81).”
In January, CISA ordered U.S. federal businesses to patch the CVE-2023-6548 code injection and the CVE-2023-6549 buffer overflow Citrix Netscaler vulnerabilities sooner or later after Citrix warned they had been actively exploited as zero-days.
One other important Netscaler flaw (tracked as CVE-2023-4966 and dubbed Citrix Bleed) was exploited as a zero-day by a number of hacking teams to breach authorities organizations and high-profile tech corporations, similar to Boeing, earlier than being patched in October.
The Well being Sector Cybersecurity Coordination Heart (HHS’ cybersecurity crew) additionally warned well being organizations in a sector-wide alert to safe NetScaler ADC and NetScaler Gateway cases in opposition to surging ransomware assaults.