A never-before-seen botnet referred to as Goldoon has been noticed concentrating on D-Hyperlink routers with an almost decade-old essential security flaw with the objective of utilizing the compromised units for additional assaults.
The vulnerability in query is CVE-2015-2051 (CVSS rating: 9.8), which impacts D-Hyperlink DIR-645 routers and permits distant attackers to execute arbitrary instructions via specifically crafted HTTP requests.
“If a focused machine is compromised, attackers can acquire full management, enabling them to extract system info, set up communication with a C2 server, after which use these units to launch additional assaults, resembling distributed denial-of-service (DDoS),” Fortinet FortiGuard Labs researchers Cara Lin and Vincent Li mentioned.
Telemetry knowledge from the community security firm factors to a spike within the botnet exercise round April 9, 2024.
All of it begins with the exploitation of CVE-2015-2051 to retrieve a dropper script from a distant server, which is answerable for answerable for downloading the next-stage payload for various Linux system architectures, together with aarch64, arm, i686, m68k, mips64, mipsel, powerpc, s390x, sparc64, x86-64, sh4, riscv64, DEC Alpha, and PA-RISC.

The payload is subsequently launched on the compromised machine and acts as a downloader for the Goldoon malware from a distant endpoint, after which the dropper removes the executed file after which deletes itself in a bid to cowl up the path and fly beneath the radar.
Any try and entry the endpoint straight by way of an internet browser shows the error message: “Sorry, you’re an FBI Agent & we won’t provide help to 
Goldoon, in addition to organising persistence on the host utilizing varied autorun strategies, establishes contact with a command-and-control (C2) server to await instructions for follow-up actions.
This contains an “astounding 27 totally different strategies” to tug off DDoS flood assaults utilizing varied protocols like DNS, HTTP, ICMP, TCP, and UDP.
“Whereas CVE-2015-2051 shouldn’t be a brand new vulnerability and presents a low assault complexity, it has a essential security impression that may result in distant code execution,” the researchers mentioned.
The event comes as botnets proceed to evolve and exploit as many units as attainable, whilst cybercriminals and superior persistent menace (APT) actors alike have demonstrated an curiosity in compromised routers to be used as an anonymization layer.
“Cybercriminals hire out compromised routers to different criminals, and more than likely additionally make them obtainable to industrial residential proxy suppliers,” cybersecurity firm Pattern Micro mentioned in a report.
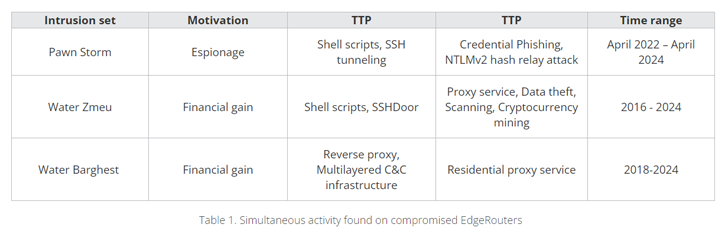
“Nation-state menace actors like Sandworm used their very own devoted proxy botnets, whereas APT group Pawn Storm had entry to a legal proxy botnet of Ubiquiti EdgeRouters.”
In utilizing the hacked routers as proxies, the target is to cover traces of their presence and make detection of malicious actions harder by mixing their exercise in with benign regular site visitors.
Earlier this February, the U.S. authorities took steps to dismantle components of a botnet referred to as MooBot that, amongst different internet-facing units like Raspberry Pi and VPS servers, primarily leveraged Ubiquiti EdgeRouters.

Pattern Micro mentioned it noticed the routers getting used for Safe Shell (SSH) brute forcing, pharmaceutical spam, using server message block (SMB) reflectors in NTLMv2 hash relay assaults, proxying stolen credentials on phishing websites, multi-purpose proxying, cryptocurrency mining, and sending spear phishing emails.
Ubiquiti routers have additionally come beneath assault from one other menace actor that infects these units with a malware dubbed Ngioweb, that are then used as exit nodes in a commercially obtainable residential proxy botnet.
The findings additional underscore the usage of varied malware households to wrangle the routers right into a community that menace actors may management, successfully turning them into covert listening posts able to monitoring all community site visitors.
“Web routers stay a well-liked asset for menace actors to compromise since they typically have diminished security monitoring, have much less stringent password insurance policies, will not be up to date ceaselessly, and should use highly effective working methods that permits for set up of malware resembling cryptocurrency miners, proxies, distributed denial of service (DDoS malware), malicious scripts, and net servers,” Pattern Micro mentioned.




