A brand new phishing marketing campaign has been noticed leveraging a novel loader malware to ship an data stealer and keylogger referred to as Agent Tesla.
Trustwave SpiderLabs mentioned it recognized a phishing e-mail bearing this assault chain on March 8, 2024. The message masquerades as a financial institution fee notification, urging the person to open an archive file attachment.
The archive (“Financial institution Handlowy w Warszawie – dowód wpłaty_pdf.tar.gz”) conceals a malicious loader that prompts the process to deploy Agent Tesla on the compromised host.
“This loader then used obfuscation to evade detection and leveraged polymorphic habits with advanced decryption strategies,” security researcher Bernard Bautista mentioned in a Tuesday evaluation.
“The loader additionally exhibited the potential to bypass antivirus defenses and retrieved its payload utilizing particular URLs and person brokers leveraging proxies to additional obfuscate site visitors.”
The tactic of embedding malware inside seemingly benign recordsdata is a tactic that has been repeatedly employed by risk actors to trick unsuspecting victims into triggering the an infection sequence.

The loader used within the assault is written in .NET, with Trustwave discovering two distinct variants that every make use of a distinct decryption routine to entry its configuration and in the end retrieve the XOR-encoded Agent Tesla payload from a distant server.
In an effort to evade detection, the loader can also be designed to bypass the Home windows Antimalware Scan Interface (AMSI), which presents the flexibility for security software program to scan recordsdata, reminiscence, and different knowledge for threats.
It achieves this by “patching the AmsiScanBuffer perform to evade malware scanning of in-memory content material,” Bautista defined.
The final section includes decoding and executing Agent Tesla in reminiscence, permitting the risk actors to stealthily exfiltrate delicate knowledge through SMTP utilizing a compromised e-mail account related to a legit security system provider in Turkey (“merve@temikan[.]com[.]tr”).
The strategy, Trustwave mentioned, not solely doesn’t increase any pink flags, but in addition affords a layer of anonymity that makes it tougher to hint the assault again to the adversary, to not point out save the trouble of getting to arrange devoted exfiltration channels.
“[The loader] employs strategies like patching to bypass Antimalware Scan Interface (AMSI) detection and dynamically load payloads, guaranteeing stealthy execution and minimizing traces on disk,” Bautista mentioned. “This loader marks a notable evolution within the deployment techniques of Agent Tesla.”
The disclosure comes as BlueVoyant uncovered one other phishing exercise carried out by a cybercrime group referred to as TA544 that leverages PDFs dressed up as authorized invoices to propagate WikiLoader (aka WailingCrab) and set up connections with command-and-control (C2) server that nearly solely encompasses hacked WordPress websites.
It is value noting that TA544 additionally weaponized a Home windows security bypass flaw tracked as CVE-2023-36025 in November 2023 to distribute Remcos RAT through a distinct loader household dubbed IDAT Loader, permitting it to grab management of contaminated techniques.
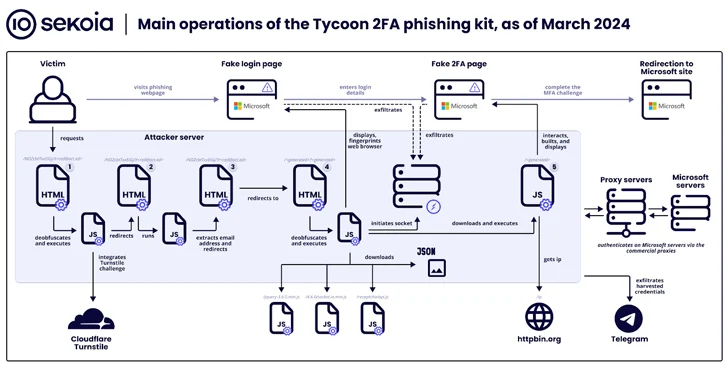
The findings additionally observe a surge in the usage of a phishing equipment referred to as Tycoon, which Sekoia mentioned has “develop into some of the widespread [adversary-in-the-middle] phishing kits over the previous few months, with greater than 1,100 domains detected between late October 2023 and late February 2024.”

Tycoon, publicly documented by Trustwave final month, permits cyber criminals to focus on customers of Microsoft 365 with phony login pages to seize their credentials, session cookies, and two-factor authentication (2FA) codes. It is identified to be energetic since a minimum of August 2023, with the service supplied through personal Telegram channels.
The phishing equipment is notable for incorporating intensive site visitors filtering strategies to thwart bot exercise and evaluation makes an attempt, requiring website guests to finish a Cloudflare Turnstile problem earlier than redirecting customers to a credential harvesting web page.
Tycoon additionally shares operational and design-level similarities with the Dadsec OTT phishing equipment, elevating the likelihood that the builders had entry to and tweaked the supply code of the latter to go well with their wants. That is supported by the truth that Dadsec OTT had its supply code leaked in October 2023.
“The developer enhanced stealth capabilities in the latest model of the phishing equipment,” Sekoia mentioned. “The current updates might scale back the detection charge by security merchandise of the Tycoon 2FA phishing pages and the infrastructure. Moreover, its ease of use and its comparatively low value make it fairly widespread amongst risk actors.”




