In at the moment’s quickly evolving SaaS atmosphere, the main focus is on human customers. This is without doubt one of the most compromised areas in SaaS security administration and requires strict governance of person roles and permissions, monitoring of privileged customers, their stage of exercise (dormant, energetic, hyperactive), their kind (inside/ exterior), whether or not they’re joiners, movers, or leavers, and extra.
Not surprisingly, security efforts have primarily been human-centric. Configuration choices embrace instruments like MFA and SSO for human authentication. Position-based entry management (RBAC) limits the extent of entry; password complexity tips block unauthorized people from accessing the appliance.
But, on the earth of SaaS, there isn’t any scarcity of entry granted to non-human actors, or in different phrases, third occasion related apps.
Service accounts, OAuth authorizations, and API keys are just some of the non-human identities that require SaaS entry. When seen by the lens of the appliance, non-human accounts are just like human accounts. They should be authenticated, granted a set of permissions, and monitored. Nevertheless, as a result of they’re non-human, significantly much less thought is given to making sure security.
Non-human Entry Examples
Integrations are most likely the best strategy to perceive non-human entry to a SaaS app. Calendly is an app that eliminates the back-and-forth emails of appointment-making by displaying a person’s availability. It integrates with a person’s calendar, reads the calendar to find out availability, and mechanically provides appointments. When integrating with Google Workspace by an OAuth authorization, it requests scopes that allow it to see, edit, share, and delete Google Calendars, amongst different scopes. The mixing is initiated by a human, however Calendly is non-human.
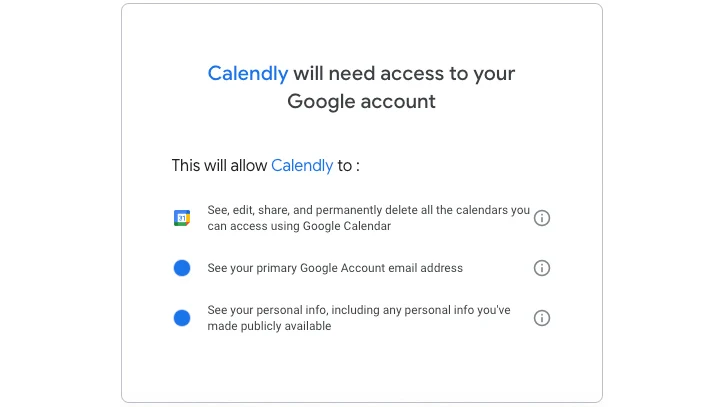 |
| Determine 1: Calendly’s required permission scopes |
Different non-human accounts contain knowledge sharing between two or extra functions. SwiftPOS is a point-of-sale (POS) utility and system for bars, eating places, and stores. Data captured by the POS is transferred to a enterprise intelligence platform, like Microsoft Energy BI, the place it’s processed and analyzed. The information is transferred from SwiftPOS to Energy BI by a non-human account.
The Problem of Securing Non-human Accounts
Managing and securing non-human accounts isn’t so simple as it sounds. For starters, each app has its personal method to managing these kinds of person accounts. Some functions, for instance, disconnect an OAuth integration when the person who approved it’s deprovisioned from the app, whereas others keep the connection.
SaaS functions additionally take totally different approaches to managing these accounts. Some embrace non-human accounts of their person stock, whereas others retailer and show the information in a special part of the appliance, making them straightforward to miss.
Human accounts may be authenticated by way of MFA or SSO. Non-human accounts, in distinction, are authenticated one time and forgotten about until there is a matter with the mixing. People even have typical habits patterns, resembling logging on to functions throughout working hours. Non-human accounts typically entry apps throughout off-peak time to scale back community site visitors and stress. When a human logs into their SaaS at 3 AM, it might set off an investigation; when a non-human hits the community at 3 AM, it is merely enterprise as traditional.
In an effort to simplify non-human account administration, many organizations use the identical API key for all integrations. To facilitate this, they grant broad permission units to the API key to cowl all of the potential wants of the group. Different occasions, a developer will use their very own high-permission API key to grant entry to the non-human account, enabling it to entry something inside the utility. These API keys operate as all-access passes utilized by a number of integrations, making them extremely tough to manage.
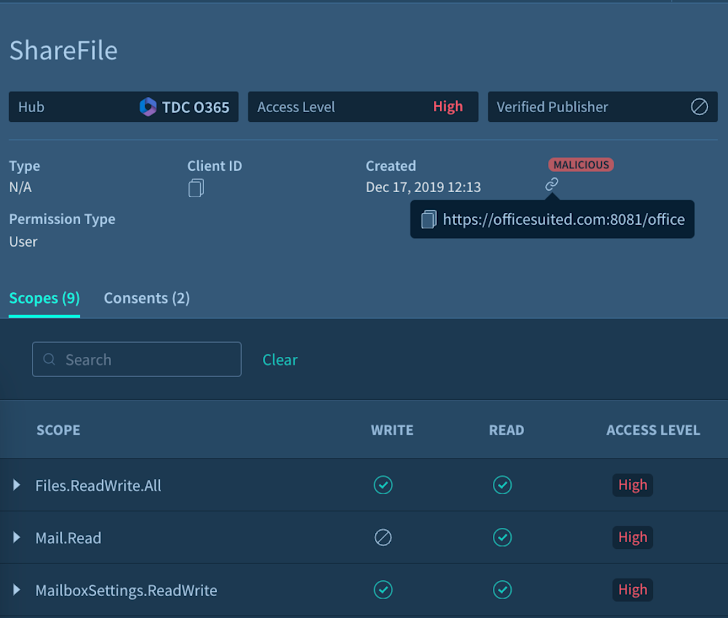 |
| Determine 2: A Malicious OAuth Software detected by Adaptive Protect’s SSPM |
Join THN’s upcoming Webinar: Actuality Test: Id Safety for Human and Non-Human Identities
The Danger Non-human Accounts Add to SaaS Stack
Non-human accounts are largely unmonitored and have wide-ranging permission scopes. This makes them a horny goal for menace actors. By compromising any of those accounts, menace actors can enter the appliance undetected, resulting in breaches, unauthorized modifications, or disruptions in service.
Taking Steps to Safe Non-human Accounts
Utilizing a SaaS Safety Posture Administration (SSPM) platform in live performance with Id Risk Detection & Response (ITDR) options, organizations can successfully handle their non-human accounts and detect once they behave anomalously.
Non-human accounts require the identical visibility by security groups as human accounts and needs to be managed in the identical person stock as their human counterparts. By unifying identification administration, it’s far simpler to view entry and permissions and replace accounts no matter who the proprietor is. It additionally ensures a unified method to account administration. Organizational insurance policies, resembling prohibiting account sharing, needs to be utilized throughout the board. Non-human accounts needs to be restricted to particular IP addresses which are pre-approved on an enable checklist, and shouldn’t be granted entry by the usual login screens (UI login). Moreover, permissions needs to be tailor-made to satisfy their particular wants as apps, and never be wide-ranging or matching their human counterparts.
ITDR performs an necessary position as properly. Non-human accounts could entry SaaS apps in any respect hours of the night time, however they’re normally pretty constant of their interactions. ITDR can detect anomalies in habits, whether or not it is adjustments in schedule, the kind of knowledge being added to the appliance, or the actions being carried out by the non-human account.
The visibility supplied by SSPM into accounts and ITDR into non-human identification habits is important in managing dangers and figuring out threats. That is a vital exercise for sustaining safe SaaS functions.
Learn extra about defending in opposition to non-human identities




