A sweeping legislation enforcement operation led by the U.Okay.’s Nationwide Crime Company this week took down LockBit, the infamous Russia-linked ransomware gang that has for years wreaked havoc on companies, hospitals, and governments all over the world.
The motion noticed LockBit’s leak website downed, its servers seized, a number of arrests made, and U.S. authorities sanctions utilized in what is without doubt one of the most vital operations taken in opposition to a ransomware group up to now.
It’s additionally, undoubtedly, one of many extra novel takedowns we’ve seen, with U.Okay. authorities asserting the seizure of LockBit’s infrastructure on the group’s personal leak website, now residence to a number of particulars in regards to the gang’s inside workings — with the promise of extra to come back.
Right here’s what we’ve discovered to this point.
LockBit didn’t delete victims’ knowledge — even when they paid
It’s lengthy been suspected that paying a hacker’s ransom demand is a big gamble and never a assure that stolen knowledge will likely be deleted. Some company victims have even stated as such, saying they “can not assure” that their knowledge could be erased.
The LockBit takedown has given us affirmation that that is completely the case. The NCA revealed that a number of the knowledge discovered on LockBit’s seized methods belonged to victims who had paid a ransom to the menace actors, “evidencing that even when a ransom is paid, it doesn’t assure that knowledge will likely be deleted, regardless of what the criminals have promised,” the NCA stated in a press release.
Even ransomware gangs fail to patch vulnerabilities
Sure, even ransomware gangs are sluggish to patch software program bugs. In line with malware analysis group vx-underground citing LockBitSupp, the alleged chief of the LockBit operation, legislation enforcement hacked into the ransomware operation’s servers utilizing a identified vulnerability within the fashionable internet coding language PHP.
The vulnerability used to compromise its servers is tracked as CVE-2023-3824, a distant execution flaw patched in August 2023, giving LockBit months to repair the bug.
“FBI f****d up servers by way of PHP, backup servers with out PHP can’t be touched,” reads LockBitSupp’s translated message to vx-underground, initially written in Russian.
Ransomware takedowns take a very long time
Since then, Europol stated that its European Cybercrime Heart, or EC3, organized greater than two-dozen operational conferences and 4 technical one-week sprints to develop the investigative leads forward of the ultimate section of the investigation: this week’s takedown.
LockBit has hacked greater than 2,000 organizations
It has lengthy been identified that LockBit, which first entered the aggressive cybercrime scene in 2019, is one among, if not essentially the most prolific ransomware gangs.
Tuesday’s operation all however confirms that, and now the U.S. Justice Division has numbers to again it up. In line with the DOJ, LockBit has claimed over 2,000 victims within the U.S. and worldwide, and acquired greater than $120 million in ransom funds.
Sanctions concentrating on a key LockBit member could have an effect on different ransomware
One of many high LockBit members indicted and sanctioned on Tuesday is a Russian nationwide, Ivan Gennadievich Kondratiev, who U.S. officers allege is concerned in different ransomware gangs.
In line with the U.S. Treasury, Kondratiev additionally has ties to REvil, RansomEXX and Avaddon. Whereas RansomEXX and Avaddon are lesser-known variants, REvil was one other Russia-based ransomware variant that gained notoriety for high-profile hacks, making thousands and thousands in ransom funds by hacking U.S. community monitoring big Kaseya.
Kondratiev was additionally named a pacesetter of a newly disclosed LockBit sub-group referred to as the “Nationwide Hazard Society.” Little else is understood about this LockBit affiliate but, however the NCA promised to reveal extra within the coming days.
The sanctions successfully ban U.S.-based victims of Kondratiev’s ransomware from paying him the ransoms he calls for. Given Kondratiev has palms in at the least 5 completely different ransomware gangs, the sanctions are prone to make his life 5 occasions harder.
The British have a humorousness
Some individuals (i.e. me, a British individual) would argue that we knew this already, however the LockBit sting has proven us that the U.Okay. authorities have a humorousness.
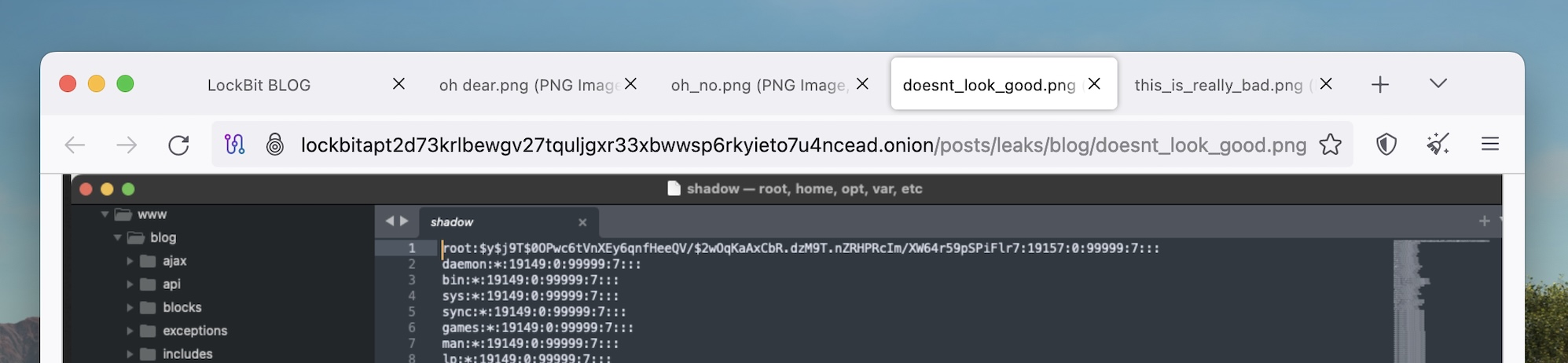
Not solely has the NCA made a mockery of LockBit by mimicking the gang’s darkish internet leak website for its personal LockBit-related revelations. We discovered numerous Easter eggs hidden on the now-seized LockBit website. Our favourite is the assorted file names for the positioning’s pictures, which embody “oh pricey.png,” “doesnt_look_good.png” and “this_is_really_bad.png.”
Picture Credit: information.killnetswitch




