Hackers are exploiting a server-side request forgery (SSRF) vulnerability in Ivanti Join Safe, Coverage Safe, and ZTA gateways to deploy the brand new DSLog backdoor on weak gadgets.
The vulnerability, tracked as CVE-2024-21893, was disclosed as an actively exploited zero-day on January 31, 2024, with Ivanti sharing security updates and mitigation recommendation.
The flaw impacts the SAML part of the talked about merchandise and permits attackers to bypass authentication and entry restricted sources on Ivanti gateways operating variations 9.x and 22.x.
The updates that repair the issue are Ivanti Join Safe variations 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2, Ivanti Coverage Safe model 22.5R1.1, and ZTA model 22.6R1.3.
On February 5, 2024, menace monitoring service Shadowserver reported seeing a number of attackers making an attempt to leverage the flaw, some utilizing proof-of-concept (PoC) exploits beforehand revealed by Rapid7, with the success charge being unknown on the time.
A brand new report by Orange Cyberdefense confirms the profitable exploitation of CVE-2024-21893 to put in a brand new backdoor named DSLog that permits the menace actors to execute instructions on compromised Ivanti servers remotely.
Orange says they first noticed this new backdoor on February 3, 2024, after analyzing a compromised equipment that had carried out the Ivanti-proposed XML mitigation (blocking all API endpoints) however hadn’t utilized the patch.
The DSLog backdoor
By analyzing the compromised Invanti gadget’s logs, Orange researchers discovered a backdoor had been injected into the equipment’s code base by issuing SAML authentication requests containing encoded instructions.
These instructions executed operations like outputting system info to a publicly accessible file (index2.txt), indicating that the attackers aimed to carry out inner reconnaissance and make sure their root entry.
Subsequent SAML requests confirmed makes an attempt to safe learn/write filesystem permissions on the breached gadget, detect modifications to a authentic logging script (DSLog.pm), and injecting the backdoor if the string indicating the modification is lacking.
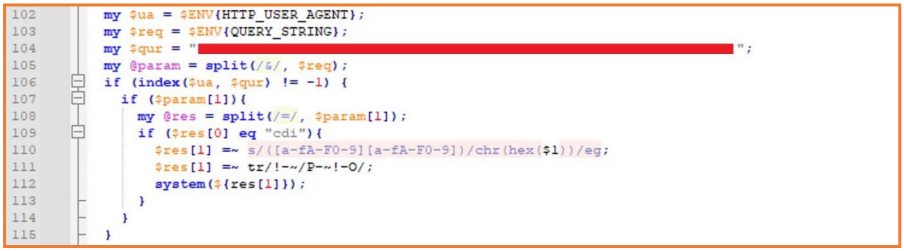
The backdoor is inserted into the DSLog file, accountable for logging numerous kinds of authenticated net requests and system logs.
The attackers employed a singular SHA256 hash per equipment as an API key, requiring this hash within the HTTP Person-Agent header for command execution. Orange explains that no hash can be utilized to contact the identical backdoor on one other gadget.
The backdoor’s predominant performance is to execute instructions as root. Orange says the DSLog backdoor can run “any instructions” on the breached gadget acquired through HTTP requests by the attackers, with the command included in a question parameter named ‘cdi.’
The HTTP requests carry the precise SHA256 hash that matches the contacted gadget, which doubles as a key to authenticate the request to the backdoor.
The researchers observe that as a result of the webshell doesn’t return standing/code when making an attempt to contact it, it’s notably stealthy.
Orange was additionally unable to find out the scheme used for the SHA256 hash calculation and famous that ‘.entry’ logs have been wiped on a number of compromised home equipment to cover the attackers’ actions.
Regardless of that, the researchers uncovered almost 700 compromised Ivanti servers by different artifacts, such because the ‘index’ textual content recordsdata within the ‘hxxp://{ip}/dana-na/imgs/’ listing.
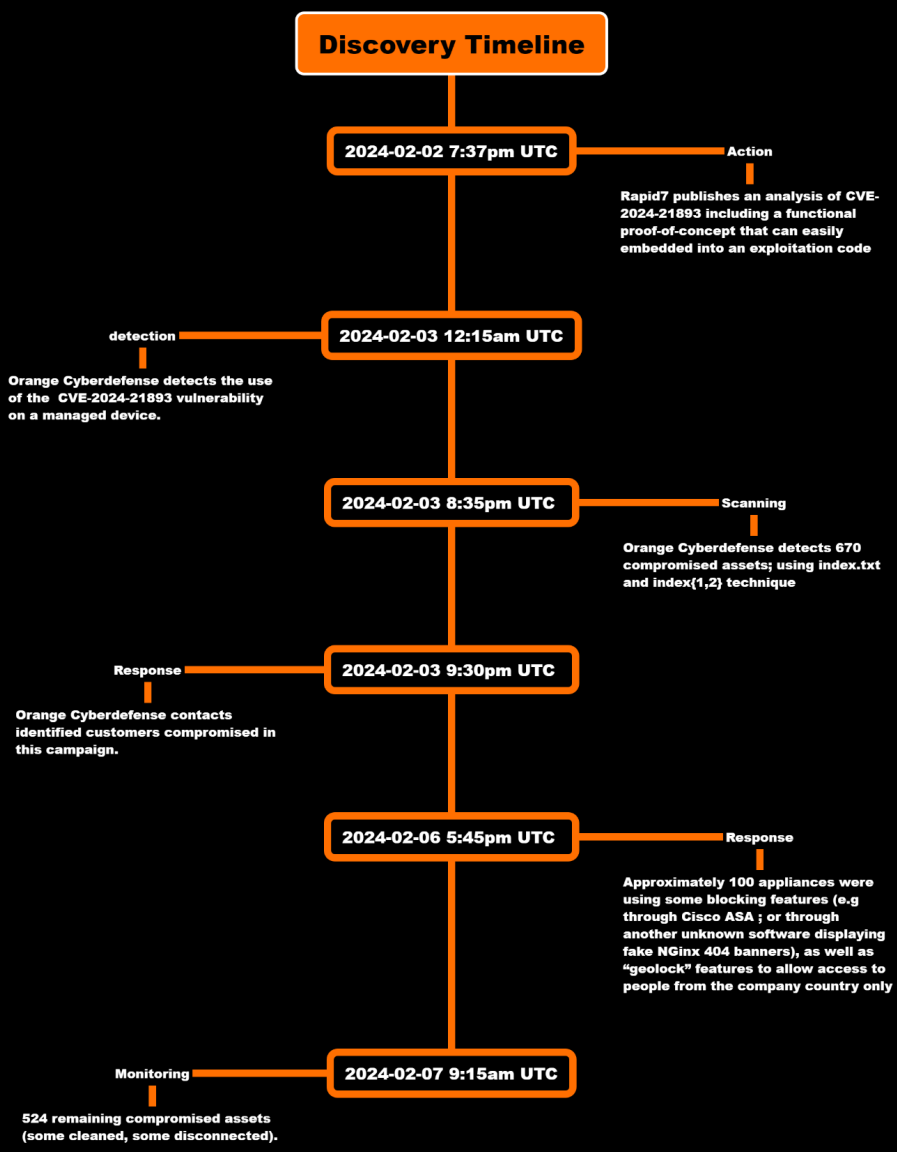
Roughly 20% of those endpoints have been already affected by earlier campaigns, whereas others have been weak solely because of the lack of extra patches or mitigations.
It is strongly recommended to comply with the newest suggestions by Ivanti to mitigate all threats concentrating on the seller’s merchandise leveraging this SSRF or any of the opposite just lately disclosed vulnerabilities impacting Ivanti gadgets.




