A essential vulnerability within the Shim Linux bootloader allows attackers to execute code and take management of a goal system earlier than the kernel is loaded, bypassing current security mechanisms.
Shim is a small open-source bootloader maintained by Pink Hat that’s designed to facilitate the Safe Boot course of on computer systems utilizing Unified Extensible Firmware Interface (UEFI).
The instrument is signed with a Microsoft key accepted by default on most UEFI motherboards that’s used to confirm the subsequent stage of the boot course of, sometimes loading the GRUB2 bootloader.
Shim was created out of necessity to permit open-source tasks similar to Linux distributions to learn from Safe Boot’s benefits, similar to stopping unauthorized or malicious code execution throughout boot, whereas nonetheless sustaining management over {hardware}.
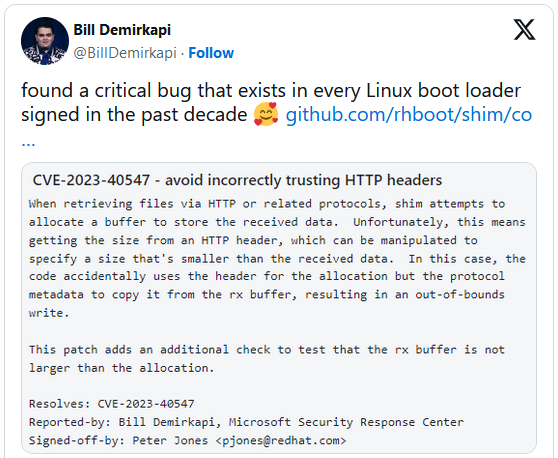
The brand new Shim flaw, tracked as CVE-2023-40547, was found by Microsoft’s security researcher Invoice Demirkapi, who first disclosed it on January 24, 2024.
The bug resides within the httpboot.c supply for Shim, which is used in addition a community picture over HTTP.
“When retrieving information through HTTP or associated protocols, shim makes an attempt to allocate a buffer to retailer the acquired knowledge,” reads the commit to repair the bug in httpboot.c.
“Sadly, this implies getting the scale from an HTTP header, which could be manipulated to specify a measurement that is smaller than the acquired knowledge.”
“On this case, the code unintentionally makes use of the header for the allocation however the protocol metadata to repeat it from the rx buffer, leading to an out-of-bounds write.”
Extra particulars in regards to the flaw grew to become out there on February 2, 2024, with Eclypsium publishing a report yesterday to attract consideration to this security drawback.
The vulnerability lies in Shim’s parsing of HTTP responses, permitting an attacker to create specifically crafted HTTP requests to trigger an out-of-bounds write.
This might permit an attacker to compromise a system by executing privileged code earlier than the working system hundreds, successfully bypassing security mechanisms applied by the kernel and the OS.
Eclypsium says a number of potential exploitation paths can leverage CVE-2023-40547, together with native, community adjoining, and distant assault factors. The agency’s report highlights the next three strategies:
A distant attacker can execute a man-in-the-middle (MiTM) assault, intercepting HTTP site visitors for HTTP boot, probably from any community place between the sufferer and the server.
A neighborhood attacker with ample privileges can modify EFI Variables or the EFI partition utilizing a reside Linux USB to change the boot order and cargo a compromised shim, executing privileged code with out disabling Safe Boot.
An attacker on the identical community can use PXE to load a compromised shim bootloader, exploiting the vulnerability.
Impression and fixes
RedHat issued a code commit to repair CVE-2023-40547 on December 5, 2023, however Linux distributions supporting Safe Boot and utilizing Shim have to push their very own patches.
Linux distributions that make the most of Shim, similar to Pink Hat, Debian, Ubuntu, and SUSE, have launched advisories with data on the flaw.
Linux customers are suggested to replace to the most recent model of Shim, v15.8, which accommodates a repair for CVE-2023-40547 and 5 different vital vulnerabilities.
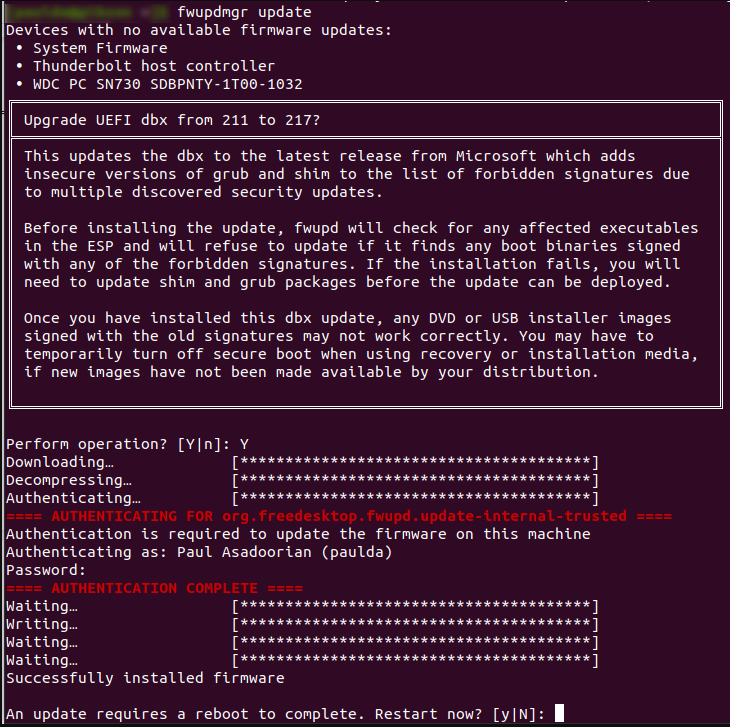
Eclypsium explains that Linux customers should additionally replace the UEFI Safe Boot DBX (revocation checklist) to incorporate the hashes of the susceptible Shim software program and signal the patched model with a sound Microsoft key.
To try this, first improve to Shim 15.8 after which apply the DBX replace utilizing the ‘fwupdmgr replace’ command (wants fwupd).
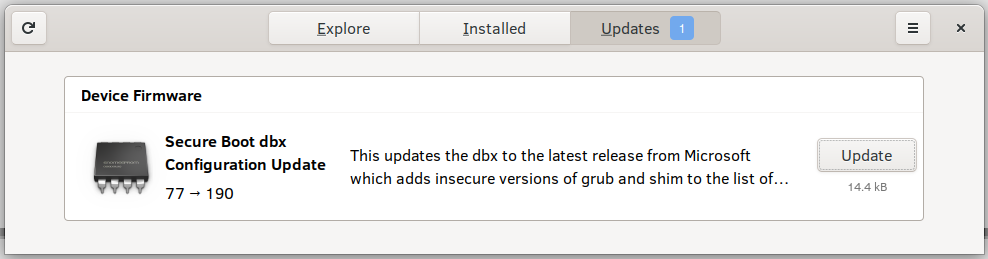
Some Linux distributions provide a GUI instrument to carry out this replace, so ensure to verify in your bundle supervisor earlier than delving into the terminal.
Though unlikely to be mass-exploited, CVE-2023-40547 is just not a bug that must be ignored, as executing code earlier than OS boot is likely one of the strongest and stealthiest types of system compromise.