Researchers discovered roughly 45,000 Jenkins cases uncovered on-line which might be susceptible to CVE-2023-23897, a vital distant code execution (RCE) flaw for which a number of public proof-of-concept (PoC) exploits are in circulation.
Jenkins is a number one open-source automation server for CI/CD, permitting builders to streamline the constructing, testing, and deployment processes. It options in depth plugin assist and serves organizations of assorted missions and sizes.
On January 24, 2024, the challenge launched variations 2.442 and LTS 2.426.3 to repair CVE-2023-23897, an arbitrary file learn drawback that may result in executing arbitrary command-line interface (CLI) instructions.
The problem arises from the CLI’s characteristic that mechanically replaces an @ character adopted by a file path with the contents of the file, a performance meant to facilitate command argument parsing.
Nevertheless, this characteristic, enabled by default, permits attackers to learn arbitrary information on the Jenkins controller’s file system.
Relying on their stage of permissions, attackers can exploit the flaw to entry delicate data, together with the primary few traces of any file and even whole information.
Because the software program vendor described within the related security bulletin, CVE-2023-23897 exposes unpatched cases to a number of potential assaults, together with RCE, by manipulating Useful resource Root URLs, “Keep in mind me” cookies, or CSRF safety bypass.
Relying on the occasion’s configuration, attackers may decrypt saved secrets and techniques, delete gadgets from Jenkins servers, and obtain Java heap dumps.
Late final week, security researchers warned of a number of working exploits for CVE-2023-23897, which dramatically elevates the danger for unpatched Jenkins servers and will increase the chance of in-the-wild exploitation.
Researchers monitoring Jenkins honeypots noticed actions that resemble real makes an attempt at exploitation, though there is no conclusive proof but.
At present, risk monitoring service Shadowserver reported that its scanners have “caught” roughly 45,000 unpatched Jenkins cases, indicating an enormous assault floor.
Many of the susceptible internet-exposed cases are in China (12,000) and america (11,830), adopted by Germany (3,060), India (2,681), France (1,431), and the UK (1,029).
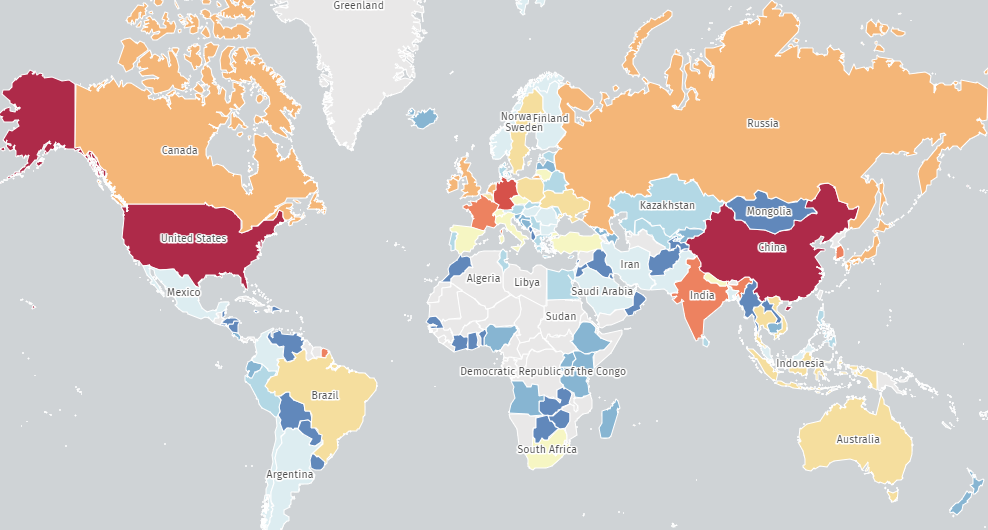
Shadowserver’s stats symbolize a dire warning to Jenkins directors, as hackers are very probably already conducting scans to search out potential targets, and CVE-2023-23897 can have extreme repercussions if efficiently exploited.
Customers unable to use the accessible security updates instantly ought to seek the advice of the Jenkins security bulletin for mitigation suggestions and potential workarounds.




