Wing Safety not too long ago introduced that fundamental third-party danger evaluation is now accessible as a free product. But it surely raises the questions of how SaaS is related to third-party danger administration (TPRM) and what corporations ought to do to make sure a correct SaaS-TPRM course of is in place. On this article we’ll share 5 tricks to handle the third-party dangers related to SaaS, however first…
What precisely is Third-Social gathering Threat Administration in SaaS?
SaaS is quickly rising, providing companies comfort, swift implementations, and beneficial alternatives. Nonetheless, this progress introduces a security problem the place dangers come up from the interconnected nature of SaaS provide chains. It’s clear that earlier than onboarding a brand new contractor or vendor, we want due diligence, security checks, and referrals. Nonetheless, we now perceive that within the SaaS area, functions are, actually, the go-to vendor of selection.
Let’s clarify: Any worker can very simply join SaaS distributors to firm knowledge, granting them permissions and entry. This straightforward onboarding is essential for effectivity, scalability, and getting work accomplished. But it surely additionally introduces loads of security points as a result of most SaaS functions, not like conventional distributors, usually bypass or skip security or IT approval.
Third-party SaaS security options play a pivotal position in safeguarding a corporation’s SaaS provide chain, and evaluating SaaS distributors turns into an important aspect of complete vendor danger administration. Whereas a number of the accountability for security falls on the SaaS vendor, organizations should keep vigilant in managing third-party dangers, no matter their dimension, to uphold a safe and strong enterprise surroundings and to make sure they adjust to business requirements.
In easy phrases, Third-Social gathering Threat Administration within the context of SaaS is the method of evaluating and managing the potential dangers posed by third-party distributors and repair suppliers within the SaaS area. TPRM helps security and IT groups establish and perceive varied sorts of dangers coming by third-party companies that relate to cybersecurity, together with knowledge privateness vulnerabilities, compliance gaps, operational points, monetary challenges, and reputational considerations.
5 TPRM ideas to make sure SaaS Safety
1. Identification and Categorization:
Figuring out and categorizing third-party connections is a vital step for organizations to know the potential threats these connections pose to security and compliance. An absence of systematic knowledge assortment and evaluation on entry ranges and vendor security can go away security and IT groups at midnight, hindering their capability to evaluate and safely use particular third-party functions appropriately.
Nonetheless, with SaaS Safety Posture Administration (SSPM) expertise, organizations can overcome this problem by simply discovering all their third-party SaaS functions. SSPM options present contextual info on the extent of entry these functions must organizational property and particulars in regards to the vendor’s security stage based mostly on steady evaluation.
 |
| Wing Safety’s TPRM answer for SaaS functions |
2. Due Diligence and Evaluation:
Conducting due diligence earlier than onboarding functions is a vital step in making certain that dangerous functions will not be being launched into a corporation’s SaaS Stack. This maximizes the necessity to assess third-party security controls, insurance policies, and procedures, making certain they meet the required requirements forward of onboarding them.
To sort out this downside, organizations ought to search for an answer that may present the required security and compliance details about related SaaS distributors/functions. Data comparable to security compliances, privateness compliances, vendor dimension, location, historic menace intelligence alerts relating to breaches or security incidents that the seller had skilled, and many others. This info is a significant a part of the due diligence technique of third-party distributors.
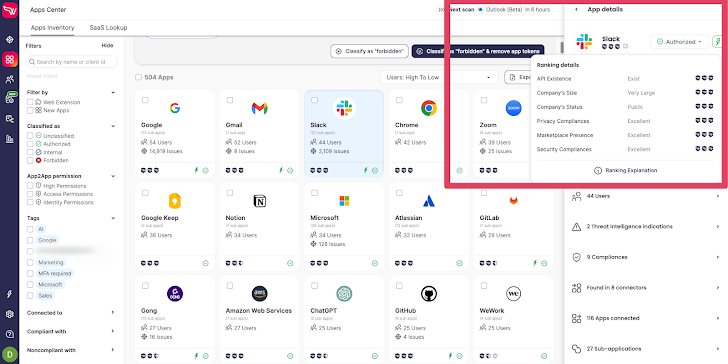 |
| Wing Safety’s free discovery answer for SaaS functions |
3. Ongoing Monitoring:
Steady monitoring is a key side of efficient TPRM. Third-party danger Administration doesn’t cease solely on the stage of prevention but in addition stresses the significance of repeatedly assessing third-party efficiency and security practices to make sure ongoing compliance and security with established requirements. This proactive method helps organizations keep forward of evolving dangers.
An efficient solution to take care of that is to have a security answer that is ready to repeatedly monitor for updates within the distributors’ info together with adjustments in security and privateness compliances, menace intelligence alerts, and its danger posture.
4. Incident Response:
Within the occasion of a security incident that pertains to a third-party connection, organizations ought to be certain that a strong incident response plan is in place. It begins by being able to obtain well timed menace intelligence alerts when breaches or security incidents happen, enabling them to reply promptly and successfully.
5. Documentation and Reporting:
Sustaining detailed data of the TPRM course of is important for demonstrating compliance with security requirements. Producing complete experiences is essential as a result of it supplies transparency and facilitates easy audits of the group’s danger administration efforts.
Organizations ought to go for an answer that may handle the stock of the complete organizational SaaS functions to this point, view all of the related info that helps the TRPM course of, and export the related experiences for audit functions.
Penalties of insufficient TPRM practices:
Failing to implement correct Third-Social gathering Threat Administration practices can have extreme penalties for organizations. Cybersecurity breaches ensuing from vulnerabilities launched by third-party distributors can result in the publicity of delicate knowledge, monetary theft, and reputational harm. Non-compliance with knowledge privateness laws can appeal to hefty fines and authorized liabilities.
What’s to realize from TPRM?
Efficient TPRM practices provide quite a few advantages. It empowers security groups to establish and deal with potential dangers, resulting in improved security and compliance. Strengthened vendor relationships improve belief and collaboration, whereas the flexibility to reveal correct due diligence helps navigate regulatory necessities extra successfully.
Finally, Third-Social gathering Threat Administration is an important course of that includes figuring out and mitigating potential vulnerabilities launched by third-party distributors. TPRM performs a significant position in strengthening a corporation’s general security posture by making certain adherence to regulatory compliance and finest security practices all through the complete SaaS provide chain.
This proactive method is important for securing organizations towards SaaS threats, because it includes evaluating the cybersecurity practices of third-party distributors to establish potential vulnerabilities and dangers within the provide chain. These assessments facilitate knowledgeable decision-making and danger mitigation and guarantee alignment with the group’s security requirements, in the end fortifying the general security defenses.
That mentioned, at this time, vendor danger assessments are vital however not sufficient. It is important to have each the capabilities to evaluate and mitigate danger. By beginning with thorough third-party danger assessments, corporations can acquire the required insights to take the subsequent steps in proactively addressing dangers and making certain a safe and well-protected SaaS provide chain.




