The Toronto Public Library (TPL) confirmed that the private data of staff, clients, volunteers, and donors was stolen from a compromised file server throughout an October ransomware assault.
Based on TPL, the attackers stole “a lot of recordsdata from a file server” containing knowledge of Toronto Public Library (TPL) and the Toronto Public Library Basis (TPLF) staff, going again to 1998.
“Data associated to those people was possible taken, together with their title, social insurance coverage quantity, date of start and residential tackle. Copies of government-issued identification paperwork offered to TPL by workers had been additionally possible taken,” the library mentioned in an replace to its incident report.
“Our cardholder and donor databases will not be affected. Nonetheless, some buyer, volunteer and donor knowledge that resided on the compromised file server could have been uncovered.”
The library has but to reveal what buyer knowledge was stolen and what number of clients had been affected by the data breach.
TPL says it hasn’t paid a ransom after the assault, and it is working with exterior cybersecurity specialists to analyze the incident. It additionally reported the breach to Ontario’s Data and Privateness Commissioner and filed a report with the Toronto Police.
As Canada’s largest public library system, TPL operates on a finances exceeding $200 million, has a membership base of 1,200,000 registered people, and gives entry to 12 million books throughout 100 department libraries all through town.
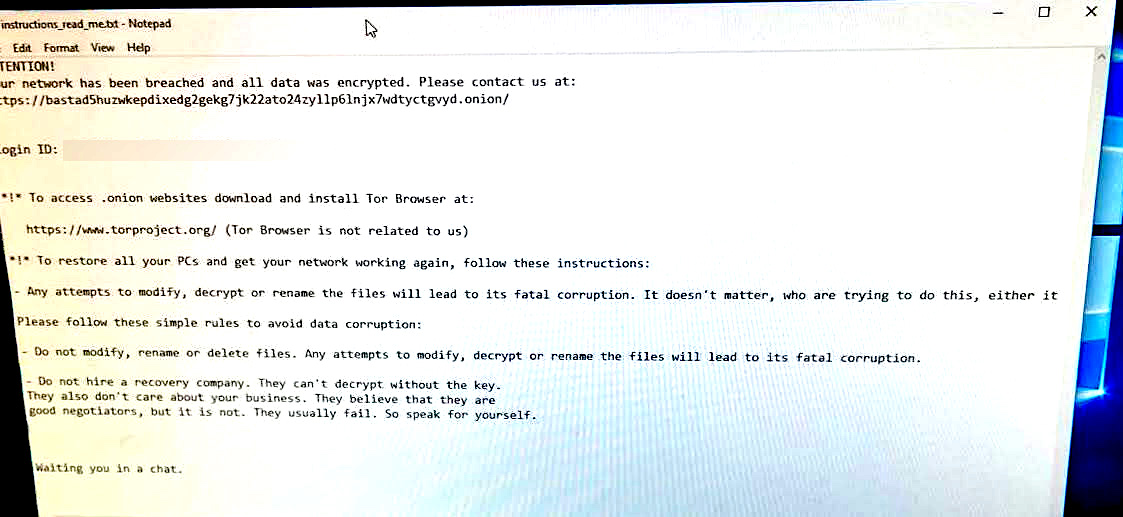
Black Basta ransomware assault
Whereas the library hasn’t but attributed the assault to a particular ransomware operation, BleepingComputer has realized that the Black Basta ransomware gang was behind the October 28 assault after seeing a photograph of a ransom word proven on a TPL workstation.
As a TPL worker advised BleepingComputer, the assault occurred in a single day on October 27, disrupting quite a few providers by Saturday morning.
We had been additionally advised that the assault had minimal impression on TPL’s electronic mail providers and did not have an effect on the library’s cellphone system. Whereas staff logged into their Workplace 365 accounts might nonetheless entry their emails, those that had been logged out could not entry their electronic mail accounts.
The group’s major servers (housing delicate knowledge) had been additionally not encrypted, hinting on the chance that the Black Basta operators did not have full entry to the library’s networks and knowledge.
As a precautionary measure to forestall the unfold of the malware, TPL shut down all different inner methods after the assault was detected.
Black Basta emerged as a Ransomware-as-a-Service (RaaS) operation in April 2022, with double-extortion assaults concentrating on many company entities.
After the Conti ransomware gang stopped working in June 2022 following a sequence of humiliating data breaches, the cybercrime syndicate fragmented into smaller factions, one among which is presumed to be Black Basta.
“The risk group’s prolific concentrating on of a minimum of 20 victims in its first two weeks of operation signifies that it’s skilled in ransomware and has a gradual supply of preliminary entry,” the Division of Well being and Human Providers security crew mentioned in March.
“The extent of sophistication by its proficient ransomware operators, and reluctance to recruit or promote on Darkish Net boards, helps why many suspect the nascent Black Basta could even be a rebrand of the Russian-speaking RaaS risk group Conti, or additionally linked to different Russian-speaking cyber risk teams.”
Furthermore, Black Basta has been linked with the FIN7 hacking group, a widely known financially motivated cybercrime group.
Because it surfaced, the Russian-speaking ransomware gang has breached and extorted a variety of high-profile victims, together with the American Dental Affiliation, Sobeys, Knauf, Yellow Pages Canada, UK outsourcing firm Capita, the Rheinmetall German protection contractor, and most just lately, U.S. authorities contractor ABB.




