Hundreds of Citrix NetScaler ADC and Gateway cases stay unpatched in opposition to a crucial vulnerability that’s being broadly exploited, security researchers warn.
The flaw, which had been exploited as a zero-day since August, is tracked as CVE-2023-4966 (CVSS rating of 9.4) and is now known as ‘Citrix Bleed’. It permits unauthenticated attackers to leak delicate info from on-prem home equipment which are configured as an AAA digital server or a gateway.
Citrix launched patches for the bug on October 10 and warned final week that risk actors are actively exploiting the vulnerability within the wild to carry out session hijacking, which permits them to fully bypass authentication, together with multi-factor authentication protections.
Over the previous few days, security researchers have began elevating the alarm on CVE-2023-4966 being broadly exploited, with a number of risk actors, together with ransomware teams, focusing on internet-accessible NetScaler ADC and Gateway cases.
The continuing mass exploitation began across the similar time Assetnote printed a technical writeup of the vulnerability and a proof-of-concept (PoC) exploit for it.
Based on security researcher Kevin Beaumont, nonetheless, the mass exploitation has not essentially been triggered by the PoC publication, as “it was clear a number of teams had already obtained technical particulars”.
By exploiting the vulnerability, attackers achieve reminiscence entry to NetScaler ADC and Gateway home equipment, which permits them to extract session cookies and try and bypass authentication. Which means that even patched cases are liable to exploitation, because the session tokens persist in reminiscence.
The compromised cookies permit the attackers to replay the classes for authentication. All they should do is kind ‘aaaaaaaaaaaaaaaaaaaaaaaa’ till they’re in, Beaumont says.
“This cookie is issued post-authentication, which may embrace multi-factor authentication checks. An attacker with entry to a sound cookie can set up an authenticated session to the NetScaler equipment with out information of the username, password, or entry to a multi-factor authentication token or machine,” Google’s cybersecurity arm Mandiant explains.
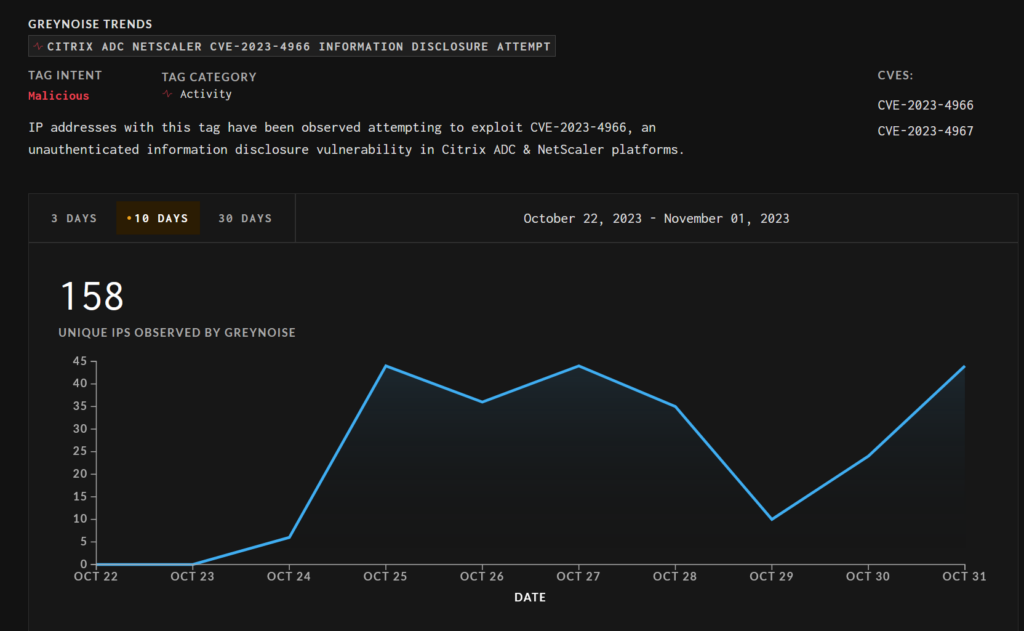
Over the weekend, Beaumont warned that attackers had stolen the session tokens of over 20,000 exploited NetScaler servers. As of November 1, information from Greynoise exhibits 158 distinctive IP addresses getting used to focus on susceptible cases over the previous 10 days.
Warning that roughly half of NetScaler clients have but to use the patches, together with telecommunication, electrical, meals, and authorities organizations, Beaumont final week printed a scanner to assist establish susceptible NetScaler servers.
To completely handle the problem, organizations ought to apply the accessible patches after which kill all lively and chronic classes, Citrix identified final week, underlining that there are not any recognized workarounds or mitigations past these advisable actions.
“In case you are utilizing an affected construct, we urge you to put in the advisable updates instantly, as this vulnerability has been recognized as crucial. We’re conscious of focused assaults within the wild utilizing this vulnerability,” the tech big stated.
On Tuesday, Mandiant stated it’s at the moment monitoring 4 risk actors actively focusing on CVE-2023-4966, compromising NetScaler servers, and performing varied post-exploitation actions.
Risk actors have deployed varied instruments for reconnaissance and credential theft, distant monitoring and administration (RMM) instruments for persistent entry, a backdoor referred to as FreeFire, living-off-the-land binaries, and utilities for lateral motion, Mandiant stated.
Based on Mandiant, as a result of NetScaler doesn’t log requests related to the bug, organizations can hunt for exploitation makes an attempt utilizing “internet utility firewalls (WAF) or different community home equipment that report HTTP/S requests directed towards the NetScaler ADC or Gateway home equipment”.
The cybersecurity agency has printed complete directions on how organizations can establish proof of session hijacking, together with indicators-of-compromise (IoCs) to help hunters.
Mandiant has seen assaults focusing on authorities, authorized {and professional} providers, and expertise organizations within the Americas, EMEA, and the APAC areas.
“Given the widespread adoption of Citrix in enterprises globally, we suspect the variety of impacted organizations is much higher and in a number of sectors,” it famous.




