The illicit replace contained a modified DLL file titled, Moserware.SecretSplitter.dll, a small a part of which is proven under:
In a security advisory, Click on Studios acknowledged:
“The compromise existed for about 28 hours earlier than it was closed down. Solely clients that carried out In-Place Upgrades between the occasions acknowledged above are believed to be affected. Handbook Upgrades of Passwordstate should not compromised. Affected clients password data might have been harvested.”
Unsurprisingly, phishing assaults in opposition to Click on Studios customers quickly adopted with attackers placing illicit hyperlinks to an up to date malware model in these emails.
Along with having a technical facet to it (i.e., the improve course of being tampered with), this provide chain assault had a social engineering facet as nicely. Within the counterfeit replace zip file, which is over 300 MB in dimension, I found the attackers had managed to change the person manuals, assist recordsdata, and PowerShell construct scripts to level to their malicious content material distribution community (CDN) server:
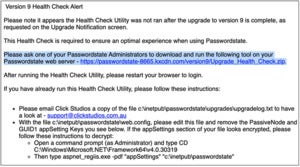
One of many assist guide paperwork stating the malicious CDN server because the official one
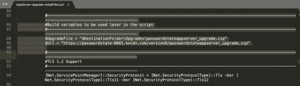
A PowerShell set up script containing malicious CDN server hyperlinks
The social engineering facet to this assault additionally demonstrates one other weak spot: that people (particularly newer builders or software program customers) might not at all times suspect hyperlinks to content material distribution networks (CDNs), whether or not these are suspicious or not. It is because CDNs are legitimately utilized by software program purposes and web sites to ship updates, scripts, and different content material.
On-line bank card skimming assaults resembling Magecart are yet one more instance of this type of provide chain assault. In some assaults, Amazon CloudFront CDN buckets have been compromised to distribute the malicious JavaScript code to a wider variety of web sites that depend on such CDNs.
3. Dependency confusion assaults
In 2021, no piece on provide chain assaults might be full with out mentioning dependency confusion, particularly due to the simplistic and automatic nature of this assault. Dependency confusion assaults work with minimal effort on the attacker’s finish and in an automatic trend as a result of an inherent design weak spot present in a number of open-source ecosystems.
Put merely, dependency confusion (or namespace confusion) works in case your software program construct makes use of a non-public, internally created dependency that doesn’t exist on a public open-source repository. An attacker is ready to register a dependency by the identical identify on a public repository, with the next model quantity. Then, very seemingly, the attacker’s (public) dependency with the upper model quantity shall be pulled into your software program construct, versus your inside dependency.

Illustration of dependency confusion weak spot puzzling a number of ecosystems
By exploiting this straightforward weak spot throughout generally used ecosystems together with PyPI, npm and RubyGems, moral hacker Alex Birsan was capable of hack into 35 massive tech corporations and stroll away with over $130,000 in bug bounty rewards.
Days following Birsan’s analysis disclosure, hundreds of dependency confusion copycat packages started flooding PyPI, npm and different ecosystems. Though most of those copycats have been created by different aspiring bug bounty hunters, some went a step too far by concentrating on recognized firms in a malicious method.
There are a number of methods to resolve dependency confusion, together with registering (reserving) the names of all of your non-public dependencies on public repositories earlier than an attacker does and utilizing automated solutions–such as a software program improvement lifecycle (SDLC) firewall that forestalls conflicting dependency names from coming into your provide chain.
House owners of open-source repositories can undertake a extra stringent verification course of and implement namespacing/scoping in place. For instance, to put up packages below the “CSO” namespace or scope, an open-source repository may confirm if the developer importing a package deal has rights to take action below the identify “CSO.”
Java element repository Maven Central employs a easy domain-based verification to confirm namespace ownership–a follow that may simply be modeled by different ecosystems. [Full disclosure: Maven Central is maintained by my employer, Sonatype].
Equally, packages printed to the Go package deal repository are named after the URL to their GitHub repository, making dependency confusion assaults rather more difficult, if not outright unimaginable.
4. Stolen SSL and code-signing certificates
With a rise in HTTPS web sites, SSL/TLS certificates are actually ubiquitously current and shield your on-line communications. A compromise of an SSL certificates’s non-public key may due to this fact threaten the safe communication and assurance provided by an end-to-end encrypted connection to the end-users.
In January 2021, Mimecast disclosed a certificates utilized by its clients to ascertain connection to Microsoft 365 Alternate providers had been compromised, probably impacting communications of about 10% of Mimecast customers. Whereas Mimecast didn’t explicitly verify whether or not this was an SSL certificates, this largely seems to be the case, as suspected by some researchers.
Whereas a compromised SSL certificates is problematic, a stolen code-signing certificates (i.e., a compromised non-public key) can have far wider penalties for software program security. Attackers who get their arms on the non-public code-signing key can probably signal their malware as an genuine software program program or replace being shipped by a good firm.
Though Stuxnet stays a major instance of a complicated assault through which attackers used stolen non-public keys from two distinguished firms to signal their malicious code as “trusted,” such assaults have flourished earlier than Stuxnet and proceed to even years later. That is additionally why the aforementioned instance of HashiCorp’s GPG non-public key publicity within the Codecov provide chain assault is problematic. Though there isn’t any indication but that HashiCorp’s compromised key was abused by attackers to signal malware, such an incident was an actual chance till the compromised key was revoked.
5. Concentrating on builders’ CI/CD infrastructure
Sonatype not too long ago noticed a multi-faceted software program provide chain assault that not solely relied on the introduction of malicious pull requests to a person’s GitHub mission, but additionally abused GitHub’s CI/CD automation infrastructure, GitHub Actions, to mine cryptocurrency. GitHub Actions offers builders with a method to schedule automated CI/CD duties for repositories hosted on GitHub.
The assault consisted of attackers cloning official GitHub repositories that used GitHub Actions, barely altering the GitHub Motion script within the repository, and submitting a pull request for the mission proprietor to merge this alteration again into the unique repository.
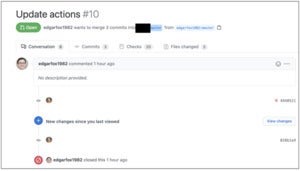
Attacker (edgarfox1982) submitting pull request for a official mission proprietor to merge altered code
Ought to a mission proprietor casually approve the altered pull request, a provide chain assault has succeeded, however that wasn’t even the prerequisite right here. The malicious pull request contained modifications to ci.yml, which have been routinely run by GitHub Actions as quickly because the pull request was filed by the attacker. The modified code primarily abuses GitHub’s servers to mine cryptocurrency.
Such an assault kills two birds with one stone: It tips a developer into accepting a malicious pull request, and may that fail, it abuses the automated CI/CD infrastructure in place for conducting malicious actions.
Likewise, researchers who efficiently breached United Nations (UN) domains and accessed over 100,000 UNEP workers file may accomplish that primarily as a result of that they had discovered uncovered Git folders and “git-credentials” recordsdata on these domains. A risk actor who obtains entry to Git credentials cannot solely clone non-public Git repositories, however probably introduce malicious code upstream to set off a provide chain assault which might have a lot harsher penalties.
The first focus of these seeking to stop provide chain assaults has been on recommending safe coding practices to builders or utilizing DevSecOps automation instruments in improvement environments. Nevertheless, securing CI/CD pipelines (e.g., Jenkins servers), cloud-native containers, and supplementary developer tooling and infrastructure has now change into simply as vital.
6. Utilizing social engineering to drop malicious code
As any security skilled is aware of, security is barely as sturdy as its weakest hyperlink. As a result of the human ingredient stays the weakest hyperlink, exploitation might come from locations the place it’s least anticipated. The Linux Basis not too long ago banned College of Minnesota researchers who have been suggesting deliberately buggy “patches” that in flip launched vulnerabilities within the Linux kernel supply code.
Though the occasion was caught and has now been handled, it demonstrates just a few easy details: Builders are unfold skinny and will not at all times have the bandwidth to vet each single code commit or a proposed code change that could be buggy or outright malicious. Extra importantly, social engineering might come from least suspected sources–in this case seemingly credible college researchers with an “.edu” electronic mail deal with.
One other current instance consists of how any collaborator contributing to a GitHub mission can alter a launch even after it’s printed. Right here once more, the expectation of a mission proprietor is that the majority contributors are submitting code and commits to their mission in good religion. It takes only one collaborator to go rogue and compromise the security of the availability chain for a lot of.
During the last 12 months, attackers creating typosquatting and brandjacking software program packages have repeatedly focused open-source builders to introduce malicious code of their upstream builds which then propagates to many customers.
All these real-world examples exhibit completely different weaknesses, assault vectors, and methods that risk actors make use of in profitable provide chain assaults. As these assaults proceed to evolve and pose challenges, extra modern options and methods are wanted when approaching software program security.




