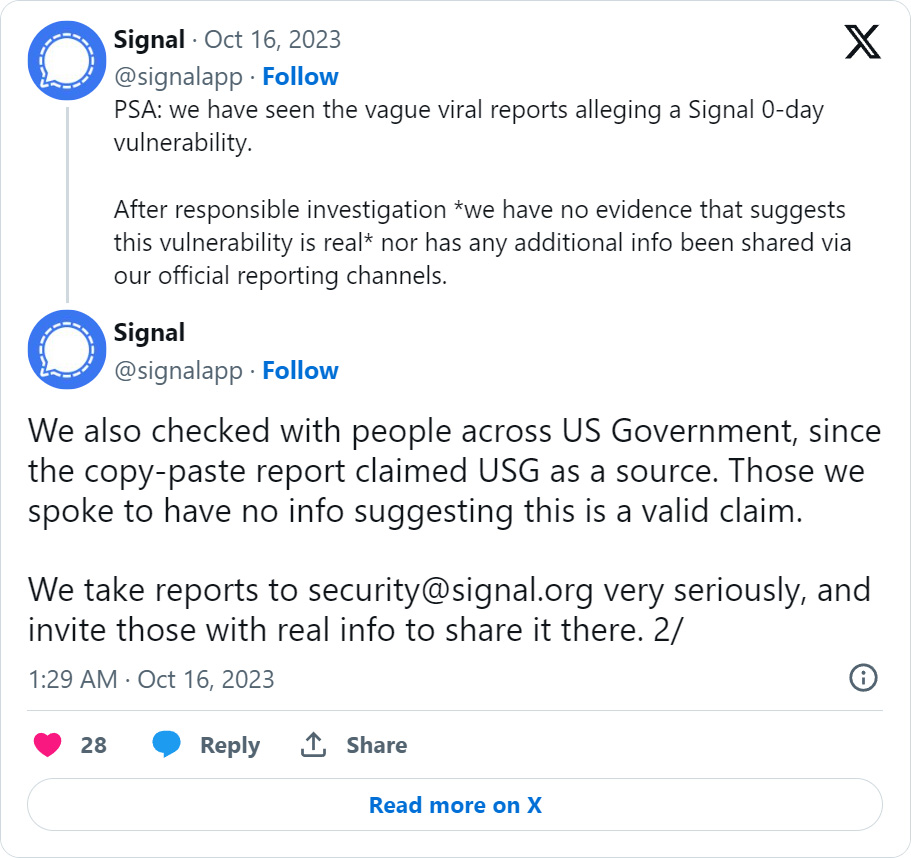
Sign messenger has investigated rumors spreading on-line over the weekend of a zero-day security vulnerability associated to the ‘Generate Hyperlink Previews’ characteristic, stating that there isn’t a proof this vulnerability is actual.
This assertion comes after quite a few sources informed BleepingComputer and reported on Twitter {that a} new zero-day vulnerability allowed for a full takeover of gadgets.
After contacting Sign concerning the zero-day final night time, they launched a press release on Twitter stating that they’ve investigated the rumors and have discovered no proof that this flaw is actual.
“PSA: we now have seen the obscure viral experiences alleging a Sign 0-day vulnerability, reads a press release on Twitter.
“After accountable investigation *we now have no proof that means this vulnerability is actual* nor has any more information been shared through our official reporting channels.”
“We additionally checked with individuals throughout US Authorities, because the copy-paste report claimed USG as a supply. These we spoke to haven’t any data suggesting it is a legitimate declare,”
Citing US authorities sources, information of the alleged zero-day rapidly unfold on-line and among the many cybersecurity neighborhood Saturday afternoon.
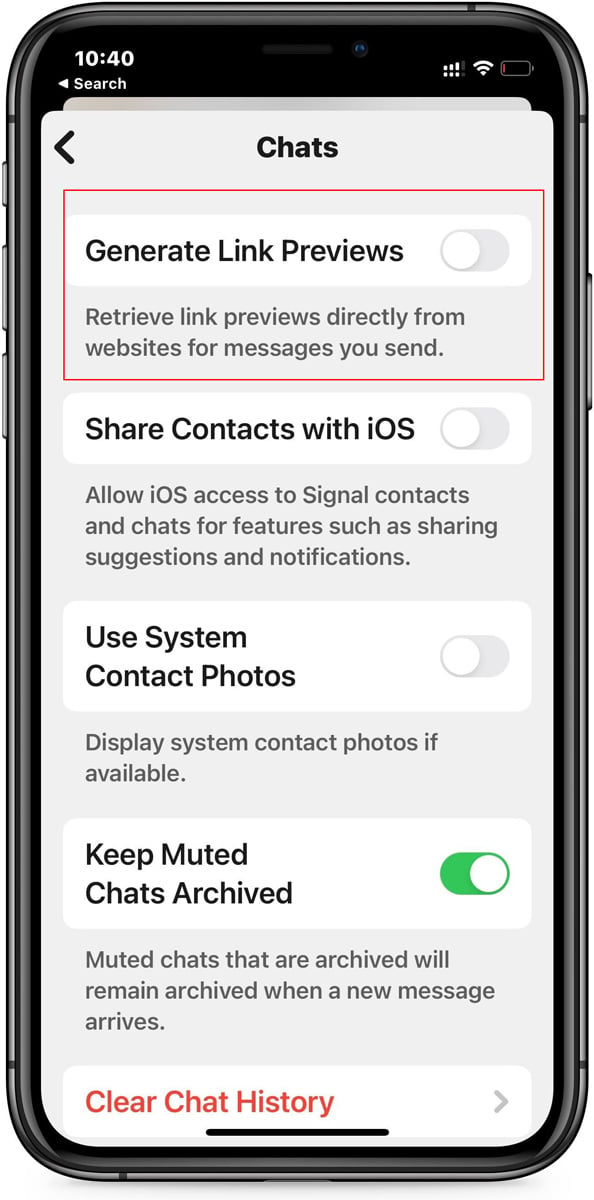
These unnamed USG sources stated that the vulnerability could possibly be mitigated by disabling the ‘Generate Hyperlink Previews’ setting in Sign.
Supply: BleepingComputer
Nonetheless, BleepingComputer couldn’t affirm the validity of those statements, regardless that we heard it from quite a few individuals claiming the identical sources.
Whereas Sign has acknowledged that they haven’t any proof of a brand new zero-day, they nonetheless request that these with new and “actual” data contact their security staff.
As that is an ongoing investigation, and the mitigation is to easily disable the Hyperlink Previews characteristic, customers might need to flip this setting off in the intervening time till it is totally confirmed to not be actual.
Sign zero-days in excessive demand
Sign zero-day bugs are extremely wanted by vulnerability brokers, who’re keen to pay a hefty quantity for flaws that may result in distant code execution on gadgets.
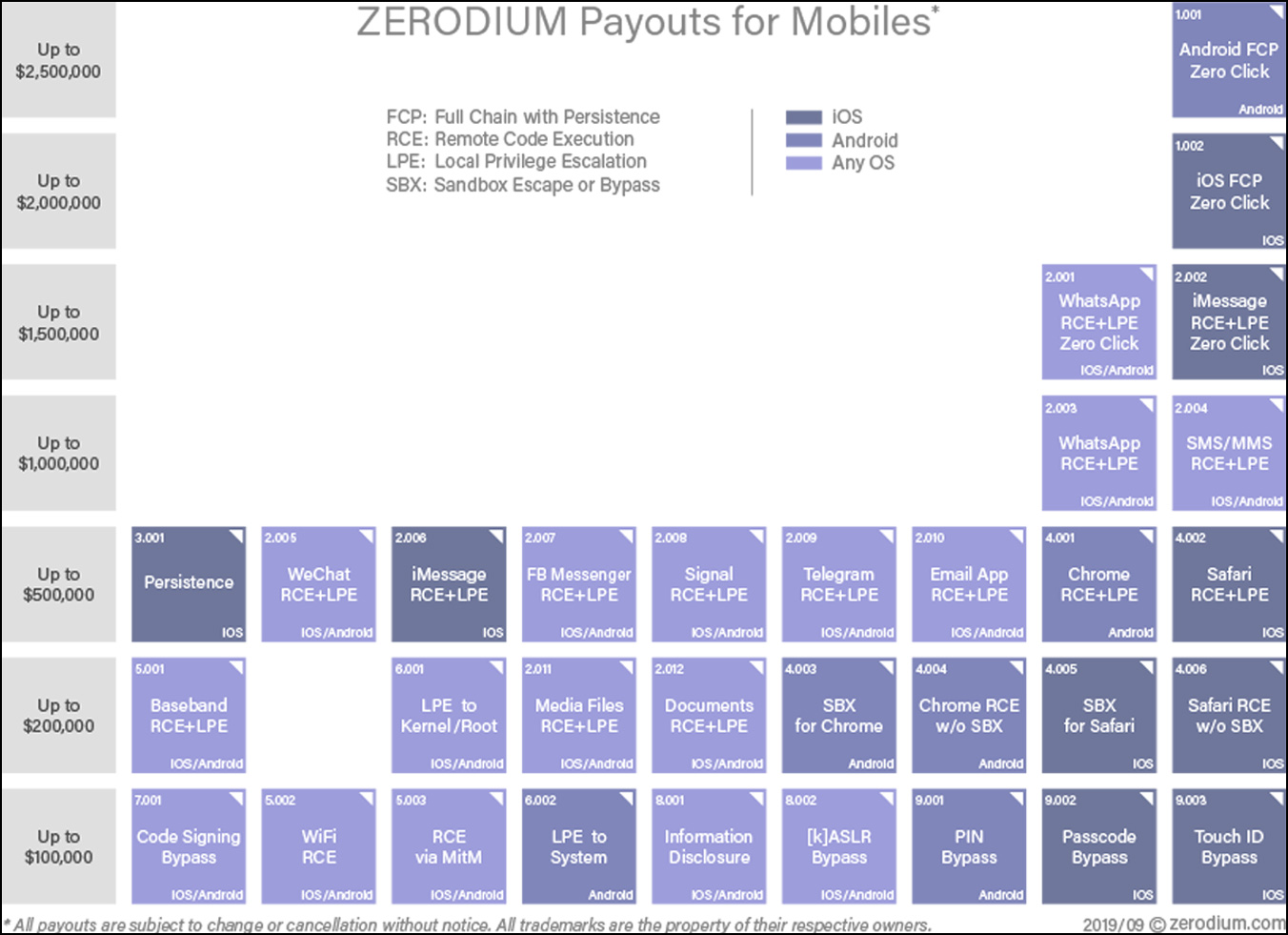
Zero-day dealer Zerodium gives as much as $500,000 for a zero-day Sign exploit chain, resulting in privilege escalation and distant code execution.
Supply: Zerodium
Nonetheless, Russian zero-day dealer Operation Zero is keen to pay as excessive as $1.5 million for a Sign zero-day distant code execution vulnerability.
Whereas each vulnerability brokers promote acquired zero-day flaws to non-public firms and authorities businesses, Operation Zero solely sells to Russian entities.
Zero-day vulnerabilities for cellular apps and working programs are in excessive demand as adware builders generally use them to put in their software program on cellular gadgets.
These providers have been discovered for use by entities, together with authorities businesses, to watch the actions of journalists, activists, and politicians.