A Mirai-based DDoS (distributed denial of service) malware botnet tracked as IZ1H9 has added 13 new payloads to focus on Linux-based routers and routers from D-Hyperlink, Zyxel, TP-Hyperlink, TOTOLINK, and others.
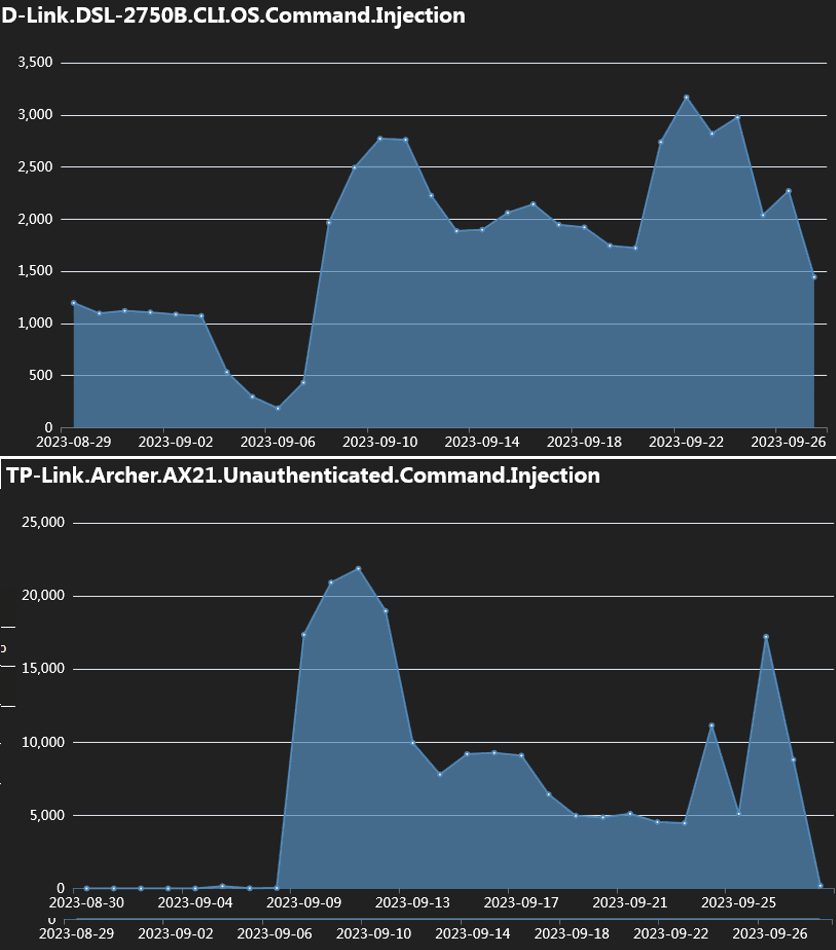
Fortinet researchers report observing a peak within the exploitation charges across the first week of September, reaching tens of 1000’s of exploitation makes an attempt towards susceptible gadgets.
IZ1H9 compromises gadgets to enlist them to its DDoS swarm after which launches DDoS assaults on specified targets, presumably on the order of purchasers renting its firepower.
Intensive IoT concentrating on
The extra gadgets and vulnerabilities focused by a DDoS malware elevated the potential to construct a big and highly effective botnet able to delivering large blows towards web sites.
Within the case of IZ1H9, Fortinet experiences it makes use of exploits for the next flaws, courting from 2015 to 2023:
- D-Hyperlink gadgets: CVE-2015-1187, CVE-2016-20017, CVE-2020-25506, CVE-2021-45382
- Netis WF2419: CVE-2019-19356
- Sunhillo SureLine (variations earlier than 8.7.0.1.1): CVE-2021-36380
- Geutebruck merchandise: CVE-2021-33544, CVE-2021-33548, CVE-2021-33549, CVE-2021-33550, CVE-2021-33551, CVE-2021-33552, CVE-2021-33553, CVE-2021-33554
- Yealink Machine Administration (DM) 3.6.0.20: CVE-2021-27561, CVE-2021-27562
- Zyxel EMG3525/VMG1312 (earlier than V5.50): CVE not specified however targets the Zyxel gadget’s /bin/zhttpd/ part vulnerability
- TP-Hyperlink Archer AX21 (AX1800): CVE-2023-1389
- Korenix JetWave wi-fi AP: CVE-2023-23295
- TOTOLINK routers: CVE-2022-40475, CVE-2022-25080, CVE-2022-25079, CVE-2022-25081, CVE-2022-25082, CVE-2022-25078, CVE-2022-25084, CVE-2022-25077, CVE-2022-25076, CVE-2022-38511, CVE-2022-25075, CVE-2022-25083
The marketing campaign additionally targets an unspecified CVE associated to the “/cgi-bin/login.cgi” route, probably affecting the Prolink PRC2402M router.
Attack chain
After exploiting one of many aforementioned CVEs, an IZ1H9 payload is injected into the gadget containing a command to fetch a shell script downloader named “l.sh” from a specified URL.
Upon execution, the script deletes logs to cover the malicious exercise, and subsequent, it fetches bot purchasers tailor-made for various system architectures.
Lastly, the script modifies the gadget’s iptables guidelines to impede connection on particular ports and make it tougher to take away the malware from the gadget.
Having accomplished all of the above, the bot establishes communication with the C2 (command and management) server and waits for instructions to execute.
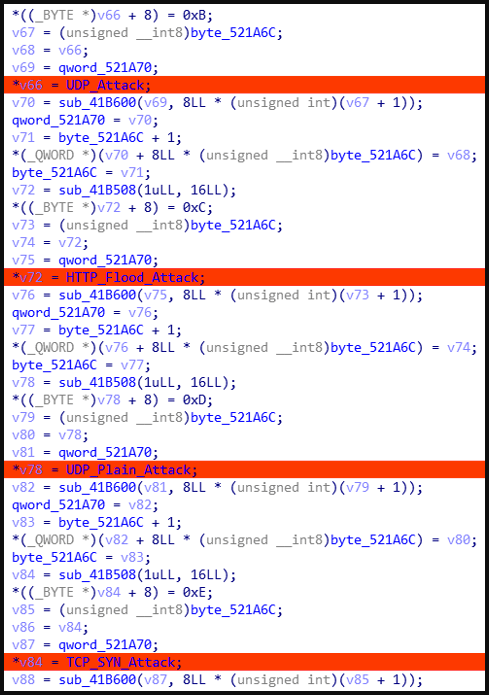
The supported instructions concern the kind of DDoS assault to launch, together with UDP, UDP Plain, HTTP Flood, and TCP SYN.
Fortinet additionally experiences that IZ1H9 contains a information part with hardcoded credentials used for brute-force assaults.
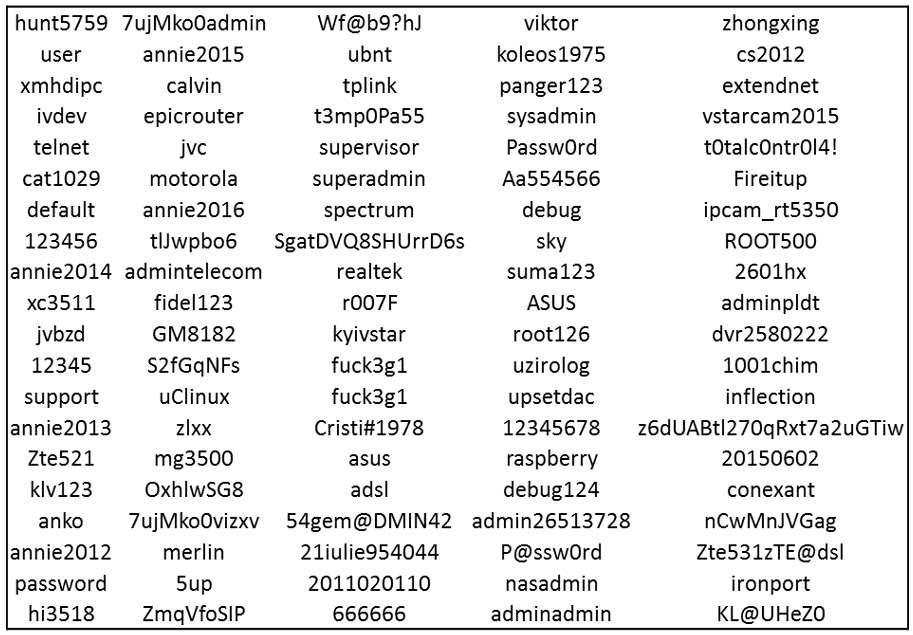
These assaults is perhaps useful for propagation to adjoining gadgets or authenticating to IoTs for which it doesn’t have a working exploit.
Homeowners of IoT gadgets are beneficial to make use of robust admin consumer credentials, replace them to the most recent obtainable firmware model, and, if doable, scale back their publicity to the general public web.




