Banking and logistics industries are beneath the onslaught of a reworked variant of a malware referred to as Chaes.
“It has undergone main overhauls: from being rewritten fully in Python, which resulted in decrease detection charges by conventional protection methods, to a complete redesign and an enhanced communication protocol,” Morphisec stated in a brand new detailed technical write-up shared with The Hacker Information.
Chaes, which first emerged in 2020, is thought to focus on e-commerce clients in Latin America, significantly Brazil, to steal delicate monetary data.
A subsequent evaluation from Avast in early 2022 discovered that the menace actors behind the operation, who name themselves Lucifer, had breached greater than 800 WordPress web sites to ship Chaes to customers of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
Additional updates had been detected in December 2022, when Brazilian cybersecurity firm Tempest Safety Intelligence uncovered the malware’s use of Home windows Administration Instrumentation (WMI) in its an infection chain to facilitate the gathering of system metadata, resembling BIOS, processor, disk measurement, and reminiscence data.
The newest iteration of the malware, dubbed Chae$ 4 in reference to debug log messages current within the supply code, packs in “vital transformations and enhancements,” together with an expanded catalog of companies focused for credential theft in addition to clipper functionalities.
Regardless of the adjustments within the malware structure, the general supply mechanism has remained the identical in assaults that had been recognized in January 2023.
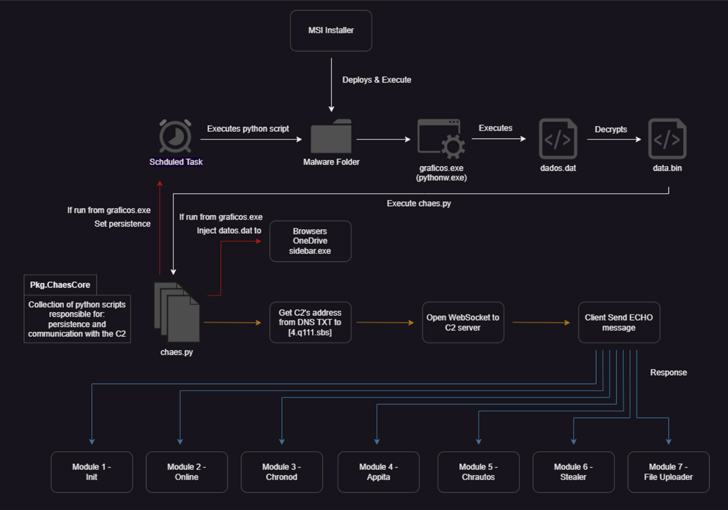
Potential victims touchdown on one of many compromised web sites are greeted by a pop-up message asking them to obtain an installer for Java Runtime or an antivirus answer, triggering the deployment of a malicious MSI file that, in flip, launches a major orchestrator module often known as ChaesCore.
The element is liable for establishing a communication channel with the command-and-control (C2) server from the place it fetches extra modules that help post-compromise exercise and knowledge theft –
- Init, which gathers in depth details about the system
- On-line, which acts as a beacon to transmit a message again to the attacker that the malware is operating on the machine
- Chronod, which steals login credentials entered in internet browsers and intercept BTC, ETH, and PIX fee transfers
- Appita, a module with related options as that of Chronod however particularly designed to focus on Itaú Unibanco’s desktop app (“itauaplicativo.exe”)
- Chrautos, an up to date model of Chronod and Appita that focuses on gathering knowledge from Mercado Libre, Mercado Pago, and WhatsApp
- Stealer, an improved variant of Chrolog which plunders bank card knowledge, cookies, autofill, and different data saved in internet browsers, and
- File Uploader, which uploads knowledge associated to MetaMask’s Chrome extension
Persistence on the host is achieved by the use of a scheduled activity, whereas C2 communications entail the usage of WebSockets, with the implant operating in an infinite loop to await additional directions from the distant server.
The focusing on of cryptocurrency transfers and prompt funds by way of Brazils’ PIX platform is a noteworthy addition that underscores the menace actors’ monetary motivations.
“The Chronod module introduces one other element used within the framework, a element referred to as Module Packer,” Morphisec defined. “This element offers the module its personal persistence and migration mechanisms, working very like the ChaesCore’s one.”
This methodology includes altering all shortcut information (LNK) related to internet browsers (e.g., Google Chrome, Microsoft Edge, Courageous, and Avast Safe Browser) to execute the Chronod module as a substitute of the particular browser.
“The malware makes use of Google’s DevTools Protocol to connect with the present browser occasion,” the corporate stated. “This protocol permits direct communication with the inside browser’s performance over WebSockets.”
“The big selection of capabilities uncovered by this protocol permits the attacker to run scripts, intercept community requests, learn POST our bodies earlier than being encrypted, and way more.”




