Mandiant has launched a scanner to test if a Citrix NetScaler Software Supply Controller (ADC) or NetScaler Gateway Equipment was compromised in widespread assaults exploiting the CVE-2023-3519 vulnerability.
The important CVE-2023-3519 Citrix flaw was found in mid-July 2023 as a zero-day, with hackers actively exploiting it to execute code remotely with out authentication on susceptible gadgets.
Per week after Citrix made security updates to handle the issue accessible, Shadowserver reported that there have been nonetheless 15,000 internet-exposed home equipment that hadn’t utilized the patches.
Nevertheless, even for organizations that put in the security updates, the danger of being compromised stays, because the patch doesn’t take away malware, backdoors, and webshells planted by the attackers within the post-compromise section.
Scanner checks for hacked gadgets
At this time, Mandiant launched a scanner that allows organizations to look at their Citrix ADC and Citrix Gateway gadgets for indicators of compromise and post-exploitation exercise.
“The instrument is designed to do a finest effort job at figuring out current compromises,” reads Mandiant’s submit.
“It won’t determine a compromise 100% of the time, and it’ll not inform you if a tool is susceptible to exploitation.”
Mandian’t Ctrix IOC Scanner should be run instantly on a tool or a mounted forensic picture, as it’s going to scan the native filesystem and configuration information for the presence of varied IOCs.
When completed, the scanner will show a abstract detailing if it encountered any indicators of compromise, as proven under.
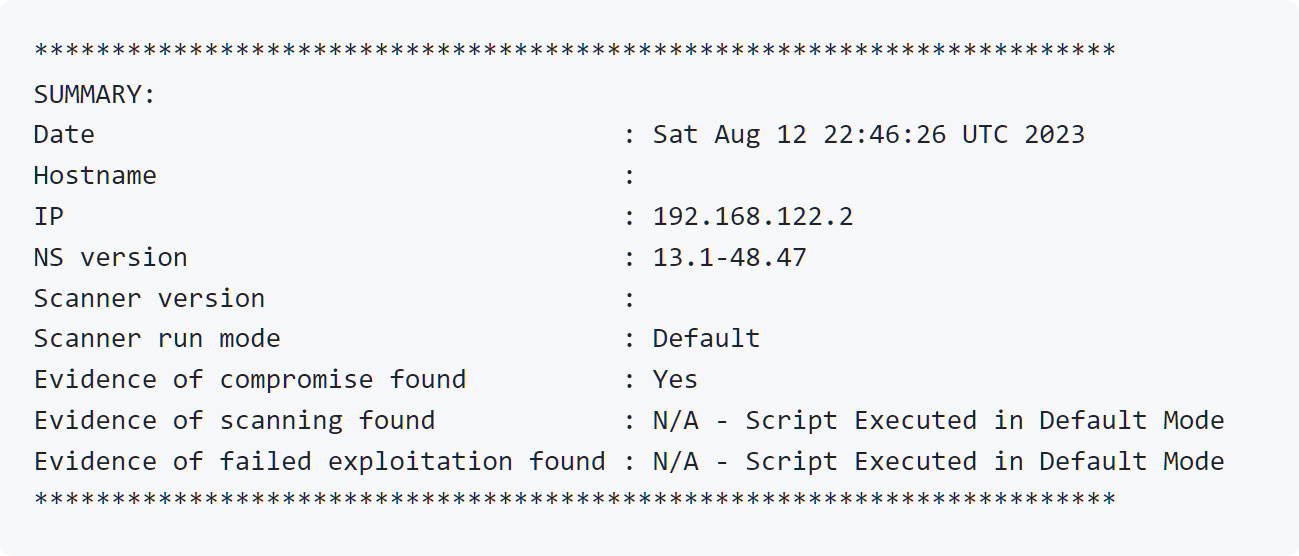
Supply: Mandiant
If it detects that the system was compromised, the scanner will show an in depth report itemizing the assorted indicators of compromise that had been detected.
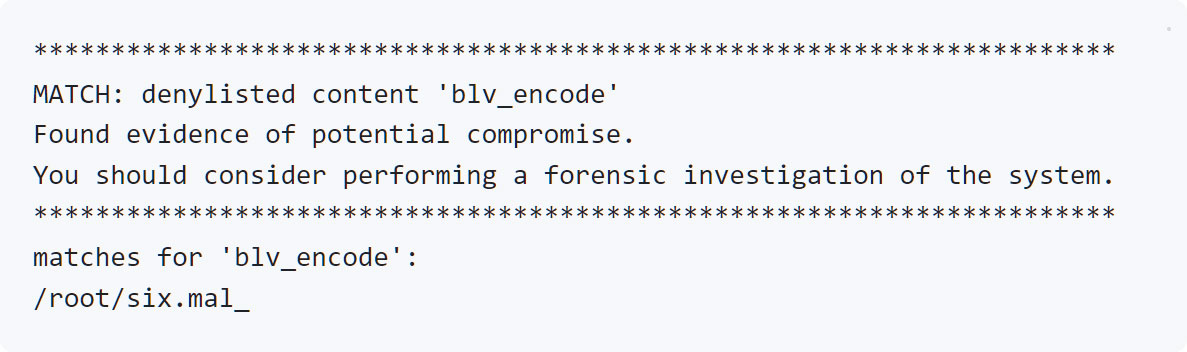
Supply: Mandiant
Among the indicators of compromise that the scanner appears to be like for on Citrix gadgets are listed under:
- File system paths containing which will include suspicious information:
- /var/netscaler/logon/LogonPoint/uiareas
- /var/netscaler/logon/LogonPoint/uiareas/*/
- /netscaler/ns_gui/epa/scripts/*/
- /netscaler/ns_gui/vpns/theme/default
- /var/vpn/themes/
- Identified attacker or suspicious instructions within the shell historical past:
- whoami$
- cat /flash/nsconfig/keys
- ldapsearch
- chmod +x /tmp
- openssl des3
- ping -c 1
- cp /bin/sh
- chmod +s /var
- echo <?php
- Recordsdata in NetScaler directories with contents matching identified IOCs:
- /var/vpn/theme/.theme.php
- /var/tmp/the
- /var/tmp/npc
- /var/tmp/conf/npc.conf
- /var/tmp/conf/multi_account.conf
- Recordsdata with suspicious permissions or possession, equivalent to uncommon setuid binaries.
- Crontab information for the ‘no person’ consumer.
- Historic cron jobs operating as ‘no person’.
- Suspicious operating processes operating as ‘no person’ or operating from ‘/var/tmp’.
Extra particulars on utilizing the scanner instrument and deciphering the outcomes might be discovered on Mandiant’s GitHub repository for the venture.
If the scanner reveals indicators of compromise, it is strongly recommended to carry out a whole forensic examination on the impacted home equipment and community elements to judge the scope and extent of the breach, which requires a unique set of instruments.
It is very important notice {that a} damaging outcome shouldn’t be taken as a assure {that a} system hasn’t been compromised, as attackers nonetheless have some ways to cover their traces and, in lots of circumstances, had ample time to take action.
“Log information on the system with proof of compromise might have been truncated or rolled, the system might have been rebooted, an attacker might have tampered with the system to take away proof of compromise and/or put in a rootkit that masks proof of compromise.” – Mandiant
It is suggested to run the scanner on all home equipment uncovered to the web whereas operating a susceptible firmware model at any time.
The scanner was designed for use with Citrix ADC and Citrix Gateway variations 12.0, 12.1, 13.0, and 13.1.




