VMware Aria Operations for Networks (previously vRealize Community Perception) is weak to a crucial severity authentication bypass flaw that might enable distant attackers to bypass SSH authentication and entry non-public endpoints.
VMware Aria is a set for managing and monitoring virtualized environments and hybrid clouds, enabling IT automation, log administration, analytics technology, community visibility, security and capability planning, and full-scope operations administration.
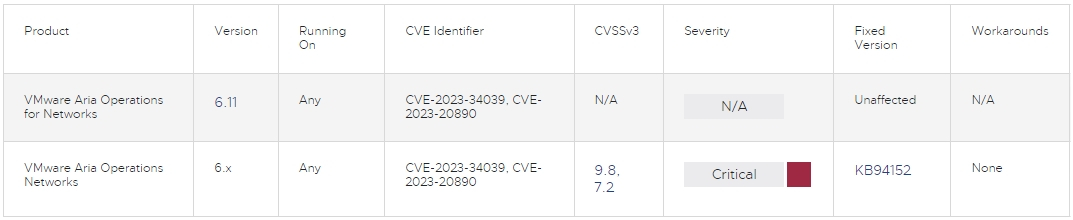
Yesterday, the seller revealed a security advisory warning of a flaw that impacts all Aria 6.x department variations.
The flaw, found by analysts at ProjectDiscovery Analysis, is tracked as CVE-2023-34039 and has obtained a CVSS v3 scope of 9.8, score it “crucial.”
“Aria Operations for Networks comprises an Authentication Bypass vulnerability as a consequence of an absence of distinctive cryptographic key technology,” warns VMware’s advisory concerning the flaw.
“A malicious actor with community entry to Aria Operations for Networks might bypass SSH authentication to achieve entry to the Aria Operations for Networks CLI.”
The exploitation of CVE-2023-34039 might result in knowledge exfiltration or manipulation by the product’s command line interface. Relying on the configuration, this entry can result in community disruption, configuration modification, malware set up, and lateral motion.
The seller has not supplied any workarounds or mitigation suggestions, so the one approach to remediate the crucial flaw is to improve to model 6.11 or apply the KB94152 patch on earlier releases.
You will discover the best security replace package deal and set up directions for the particular model you are utilizing from this webpage.
A second, high-severity (CVSS v3: 7.2) flaw addressed by the identical patch is CVE-2023-20890. This arbitrary file write drawback could enable an attacker with administrative entry to the goal to carry out distant code execution.
On account of this software program being utilized in giant organizations holding beneficial property, hackers are fast to take advantage of crucial severity flaws impacting these merchandise.
In June 2023, VMware warned its purchasers concerning the lively exploitation of CVE-2023-20887, a distant code execution vulnerability impacting Aria Operations for Networks.
The mass-scan and exploitation efforts began per week after the seller made a security replace that addressed the issue accessible and simply two days after a working PoC (proof of idea) exploit was revealed.
That mentioned, any delay in making use of the KB94152 patch or upgrading to Aria model 6.11 would put your community at vital danger of hacker assaults.




