If you hear the time period “spoofed” electronic mail, does enterprise electronic mail compromise (BEC) come to thoughts? It does for many individuals—particularly security leaders. BEC is a type of electronic mail fraud, and it has been a prime concern for chief info security officers for years.
BEC scams are a expensive downside. The most recent Web Crime Report from the FBI’s Web Crime Grievance Heart (IC3) notes that adjusted losses from BEC had been $2.9 billion final yr. Since 2013, collected monetary losses attributable to BEC have reached almost $53 billion.
Spoofing is impersonation, and it’s the essence of electronic mail fraud. It’s also one of the crucial frequent strategies utilized in different sorts of assaults like phishing and ransomware. Your enterprise, like many, in all probability focuses on stopping spoofed emails earlier than they will attain workers’ inboxes. Nevertheless, there may be extra to fret about. Spoofed electronic mail has the potential to wreck your model repute and jeopardize your enterprise ecosystem, too.
On this put up, we are going to discover varied impersonation danger situations. However first, let’s take a look at some frequent ways.
Impersonation ways
Listed here are some frequent strategies unhealthy actors use to impersonate others to allow them to additional their assaults.
- Show identify spoofing. The show identify seems within the “From:” area of an electronic mail. It’s the best electronic mail identifier to control. Attackers forge electronic mail headers in order that consumer software program shows the fraudulent sender, which most customers take at face worth.
- Area spoofing. Unhealthy actors will use an actual match of a company’s area to launch any such fraud assault. Attackers who interact in area spoofing will try and imitate the sending server or sending area.
- Lookalike domains. Third events can register lookalike domains and ship electronic mail that seems to have come from a trusted supply.
- Compromised provider accounts. In some superior assaults, attackers will compromise an account from a provider that works with the enterprise that they need to goal. They are going to use the compromised provider account to hijack the e-mail communication between their goal and its provider. Ultimately, attackers are ready to launch an assault or solicit fraudulent cost or delicate knowledge.
Attack situations
Now, let’s dive into how attackers can use spoofed emails to use the trusted relationships you’ve got along with your prospects, enterprise companions, suppliers and workers.
State of affairs 1: Impersonate you to focus on your workers
You might be in all probability most aware of the primary situation, the place attackers fake to be somebody inside your organization, like your CEO or supervisor. The rip-off typically begins with a easy lure that appears to be a benign message like: How is your day? Are you at your desk? Are you able to assist me with one thing pressing?
As soon as attackers get a sufferer to have interaction, the dialog evolves. The unhealthy actor could request the sufferer to buy reward playing cards for them, proceed with a fraudulent cost, or share confidential knowledge.
Not solely can attackers impersonate executives, however they will additionally fake to be common workers asking human assets to redirect their payrolls. In brief, it doesn’t matter what a sufferer’s function is. Anybody will be impersonated to focus on anybody inside a company.
An instance of a easy lure the place the attacker used show identify spoofing to impersonate Ken, the CEO.
Proofpoint
One other instance of a BEC lure the place an attacker used a lookalike area of Watertronics (vs. waltertronics, within the instance) to spoof their CEO.
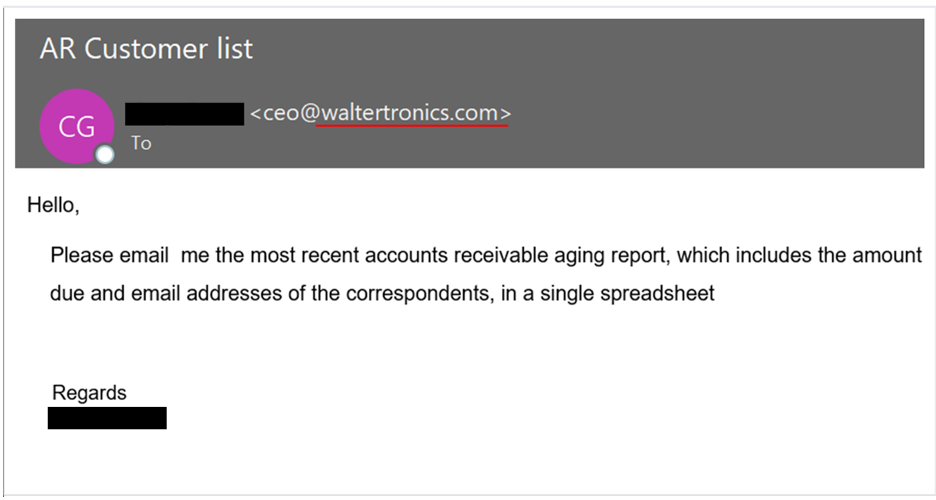
Proofpoint
State of affairs 2: Exploit your suppliers or enterprise companions to focus on your workers
The most typical theme on this situation is provider invoicing fraud. Unhealthy actors will exploit an organization’s suppliers utilizing ways reminiscent of malicious lookalike domains of suppliers or compromised provider accounts to both ship a faux bill or request the sufferer to redirect the cost to a checking account that the attackers management. (Typically, we see a number of ways used collectively in a single assault!)
This method targets business-to-business entities and may end up in important monetary losses for these corporations. It’s not extraordinary for companies to lose tens of tens of millions of {dollars}.
Compromised provider accounts are exhausting to detect. Moreover, adversaries can use this tactic in assaults aside from BEC. For instance, they will flip an bill into a chunk of malware and trick the sufferer into downloading a malicious attachment. Or they will get hold of delicate knowledge from the sufferer who believes that they’re interacting with a trusted vendor.
Whatever the finish recreation, attackers solely need to intercept the enterprise communications between you and your suppliers to realize their objectives.
An instance the place an attacker used a compromised provider account to launch a provider invoicing fraud assault.
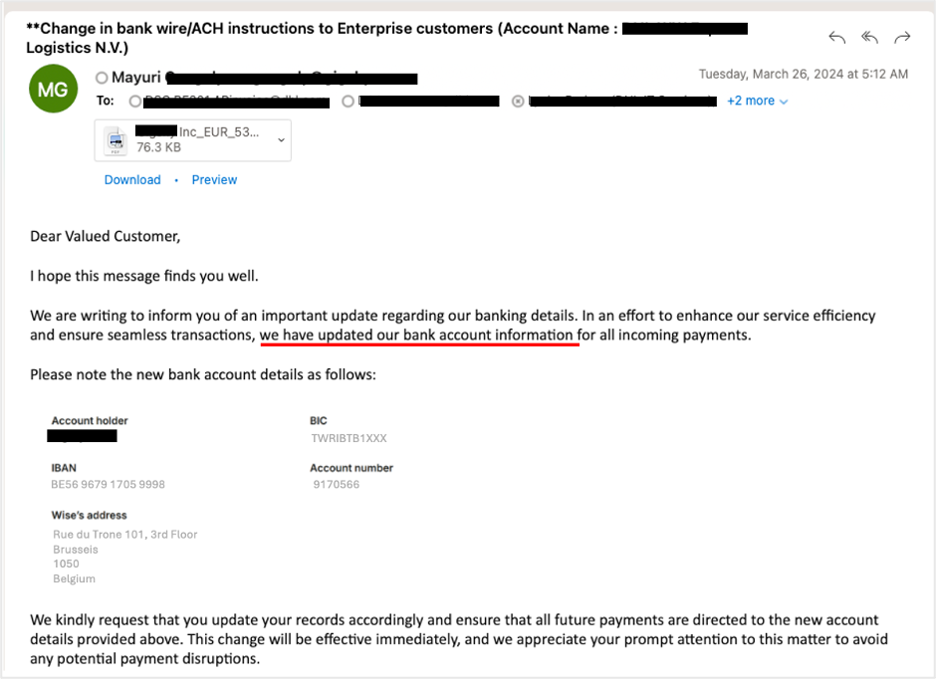
Proofpoint
State of affairs 3: Impersonate you to focus on your enterprise companions
Attackers can flip your suppliers in opposition to you—and so they can flip you in opposition to your enterprise companions. They do that by spoofing your trusted domains or by registering domains that look similar to yours. With out correct controls in place, reminiscent of electronic mail authentication, your trusted domains are weak to hijacking.
In contrast to show identify spoofing, area spoofing is far tougher to identify as a result of the fraudulent electronic mail seems to return from a professional area. At Proofpoint, we see about 23 million messages per day, on common, from unauthorized senders who doubtlessly spoof trusted domains. And registering impostor domains couldn’t be simpler for attackers. Unhealthy actors have registered as many as 300 impersonation domains in a single day to advertise a phishing marketing campaign.
An inventory of malicious lookalike domains registered by unhealthy actors to impersonate PayPal, together with the date they had been registered.
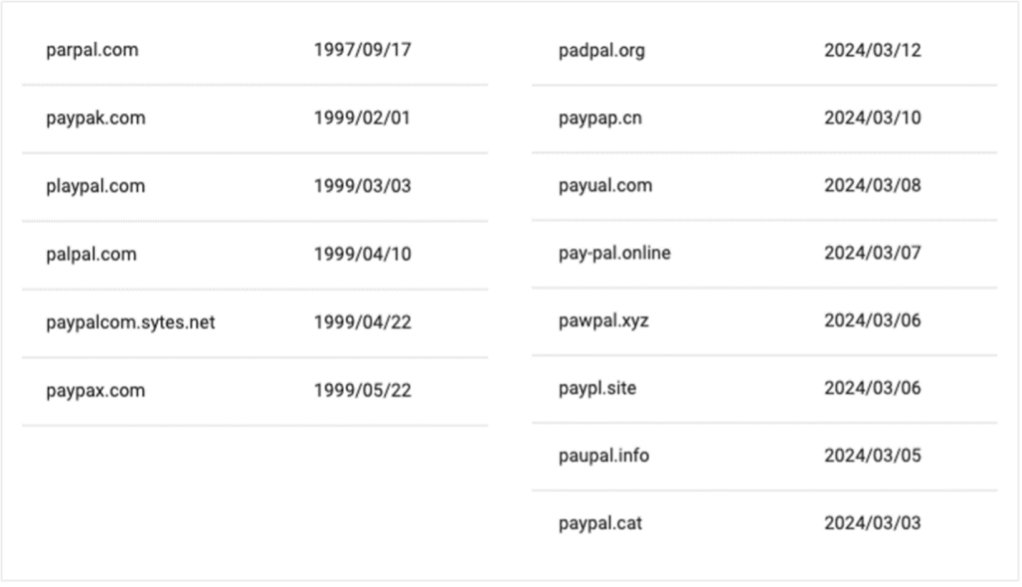
Proofpoint
Now you can begin to see the complexity of impersonation danger. This isn’t nearly threats that focus on your workers. These assaults might additionally influence your enterprise negatively by damaging your model and repute. You don’t need to be thought-about a dangerous provider by your enterprise companions. And it’s more and more probably that your enterprise companions will ask your enterprise to implement controls that may forestall model impersonation—in the event that they haven’t finished so already.
State of affairs 4: Impersonate you to focus on your prospects
Much like the third situation, attackers can impersonate you to focus on your prospects, inflicting injury to your model or repute. It’s vital to grasp that unhealthy actors not solely can impersonate your consumer electronic mail, but in addition your software electronic mail. Many corporations overlook this reality.
In contrast with the variety of transactional emails that functions generate, the variety of consumer emails is just like the tip of an iceberg. Furthermore, you’ll have a excessive variety of third-party apps, reminiscent of from software-as-a-service (SaaS) companions, sending transactional emails as “you” to your prospects (and even to your workers). For instance:
- An organization would possibly use Salesforce to ship newsletters to prospects
- Healthcare suppliers would possibly companion with a SaaS vendor to ship appointment reminders
- Retailers would possibly use third-party apps to ship order affirmation or delivery notifications
These emails are uncovered to danger if they don’t seem to be protected. Similar to consumer electronic mail, software electronic mail will be spoofed. It will probably additionally carry a malicious payload if an assault compromises an app or a SaaS supplier.
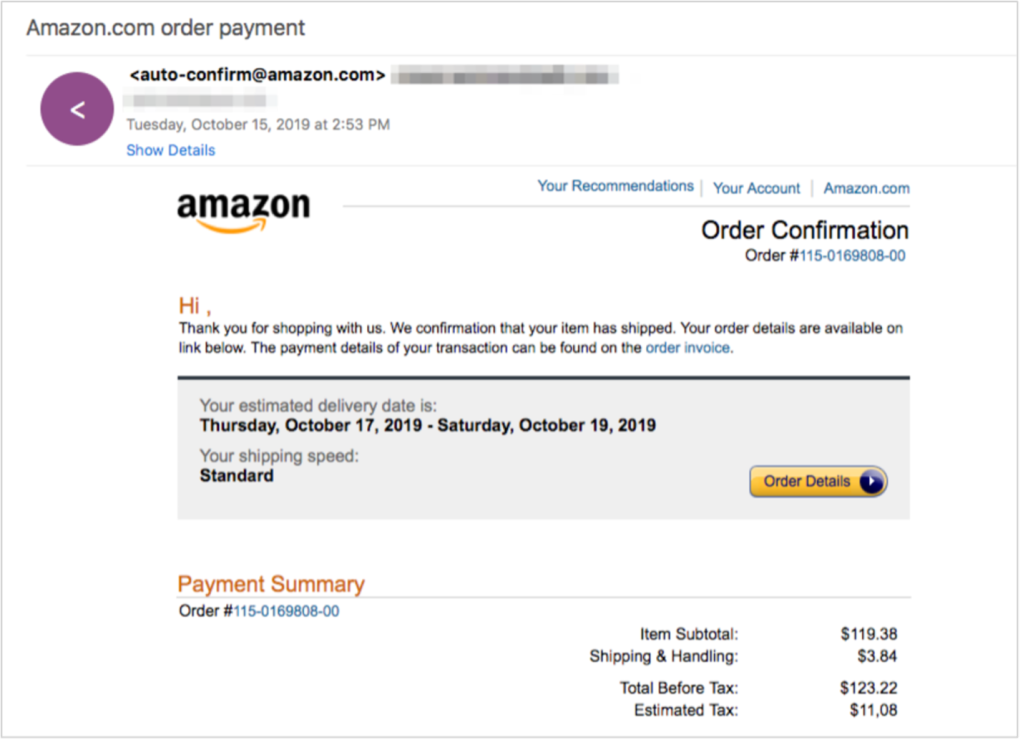
An instance of an application-generated transactional electronic mail that was spoofed by attackers.
Ideas for mitigating your impersonation danger
Impersonation danger is a pervasive downside for each enterprise. A multilayered method to protection will help you scale back that danger. A sturdy electronic mail security resolution will make it easier to cease most threats earlier than they will attain your finish customers’ inboxes. It will probably additionally detect and block all kinds of threats that contain impersonation ways, like phishing, malware, ransomware and BEC.
Listed here are some ideas for locating the suitable resolution and mitigating your danger:
- Search for superior know-how. To detect and block rising threats extra successfully, you want a contemporary electronic mail security resolution that makes use of synthetic intelligence and machine studying together with behavioral evaluation, menace intelligence and even massive language fashions (LLMs).
- Empower your workers. Since there isn’t a single know-how that may cease 100% of threats, it’s necessary to pair your menace detection resolution with a threat-driven security consciousness program. Doing so will give your workers the information that they should determine impersonation ways and themes. Additionally, bear in mind to provide them instruments to report any suspicious messages.
- Authenticate your emails. A vital facet of impersonation danger is attackers spoofing your area and abusing your model and repute. E-mail authentication is among the handiest methods to forestall area spoofing. So, search for an answer that may authenticate all of your emails, together with consumer and software emails.
- Get full visibility, together with compromised provider accounts. The answer ought to give you full visibility into any electronic mail despatched as “you.” It ought to provide the confidence to implement electronic mail authentication as effectively. When you’ve got actionable visibility into compromised provider accounts, you may higher defend in opposition to refined impersonation assaults the place adversaries truly grow to be your suppliers.
- Search for adaptive controls. Making use of adaptive controls, just like the isolation of URLs from dangerous suppliers, lets you mitigate your publicity to compromised provider accounts with out disrupting your enterprise.
Be taught extra
Proofpoint Impersonation Safety will help safeguard the belief between you and your prospects, suppliers and enterprise companions. It gives probably the most complete safety to your trusted enterprise communications in opposition to impersonation threats, with a multilayered protection.
To study extra, take a look at Proofpoint Impersonation Safety. And you’ll want to be a part of our Might 23 webinar, the place our specialists will interact in an in-depth dialogue about impersonation threats.