Over three thousand internet-exposed Apache ActiveMQ servers are weak to a just lately disclosed crucial distant code execution (RCE) vulnerability.
Apache ActiveMQ is a scalable open-source message dealer that fosters communication between purchasers and servers, supporting Java and varied cross-language purchasers and lots of protocols, together with AMQP, MQTT, OpenWire, and STOMP.
Due to the venture’s help for a various set of safe authentication and authorization mechanisms, it’s extensively utilized in enterprise environments the place techniques talk with out direct connectivity.
The flaw in query is CVE-2023-46604, a crucial severity (CVSS v3 rating: 10.0) RCE permitting attackers to execute arbitrary shell instructions by exploiting the serialized class sorts within the OpenWire protocol.
In response to Apache’s disclosure from October 27, 2023, the problem impacts the next Apache Lively MQ and Legacy OpenWire Module variations:
- 5.18.x variations earlier than 5.18.3
- 5.17.x variations earlier than 5.17.6
- 5.16.x variations earlier than 5.16.7
- All variations earlier than 5.15.16
Fixes have been made out there on the identical day with the discharge of variations 5.15.16, 5.16.7, 5.17.6, and 5.18.3, that are the beneficial improve targets.
Hundreds of servers unpatched
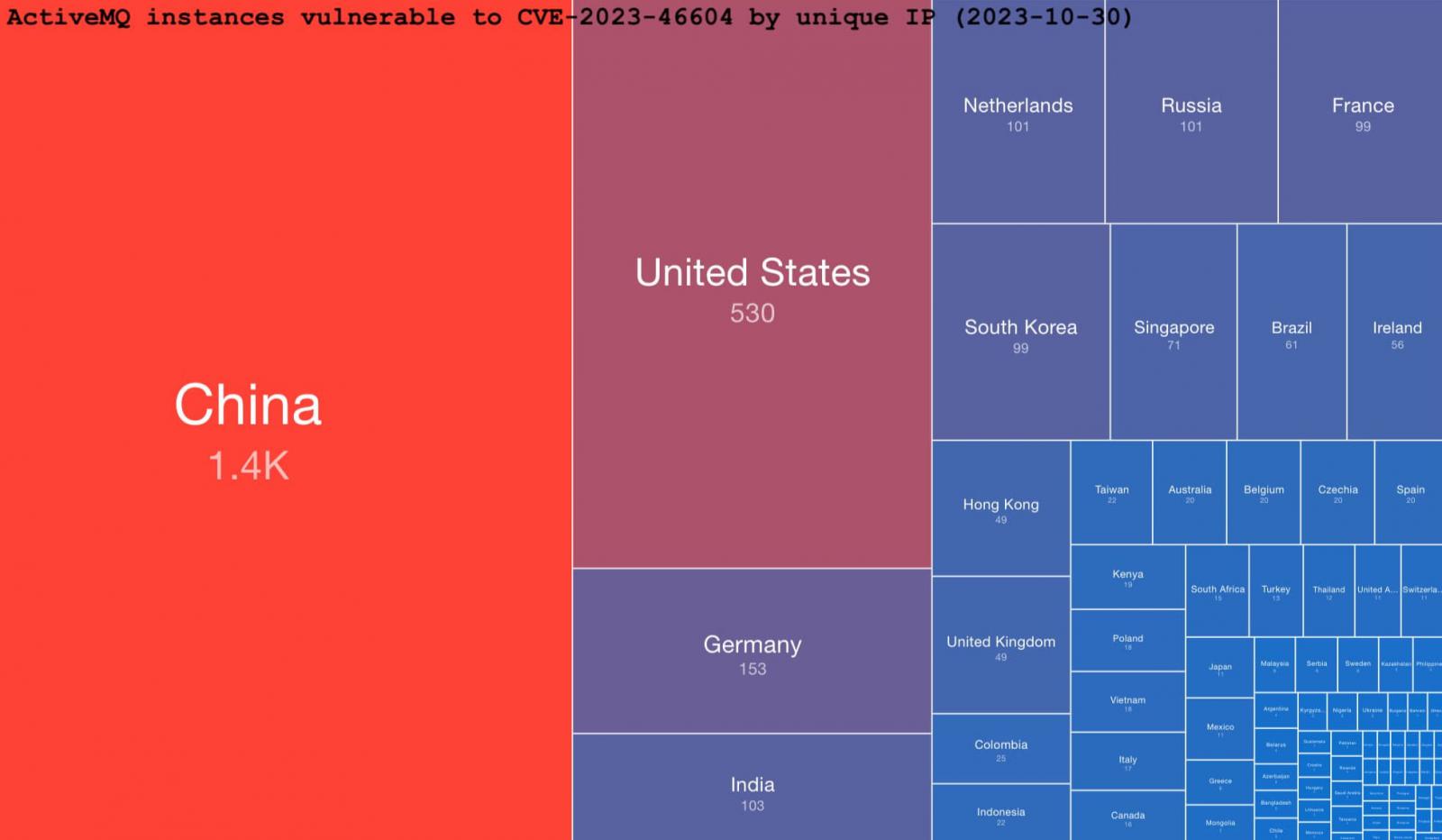
Researchers from risk monitoring service ShadowServer discovered 7,249 servers accessible with ActiveMQ companies.
Of these, 3,329 have been discovered to run an ActiveMQ model weak to CVE-2023-4660, with all of those servers weak to distant code execution.
Many of the weak situations (1,400) are situated in China. America comes second with 530, Germany is third with 153, whereas India, the Netherlands, Russia, France, and South Korea have 100 uncovered servers every.
Given the position Apache ActiveMQ fulfills as a message dealer in enterprise environments, exploitation of CVE-2023-46604 may lead to message interception, workflow disruption, information theft, and even lateral motion within the community.
As technical particulars on exploiting CVE-2023-46604 are publicly out there, making use of the security updates must be thought of time-sensitive.