AI service Cutout.Professional has suffered a data breach exposing the non-public data of 20 million members, together with e mail addresses, hashed and salted passwords, IP addresses, and names.
Cutout.Professional is an AI-powered picture and video enhancing platform for picture enhancement, background elimination, diffusion, colorizing, outdated picture restoration, and content material era.
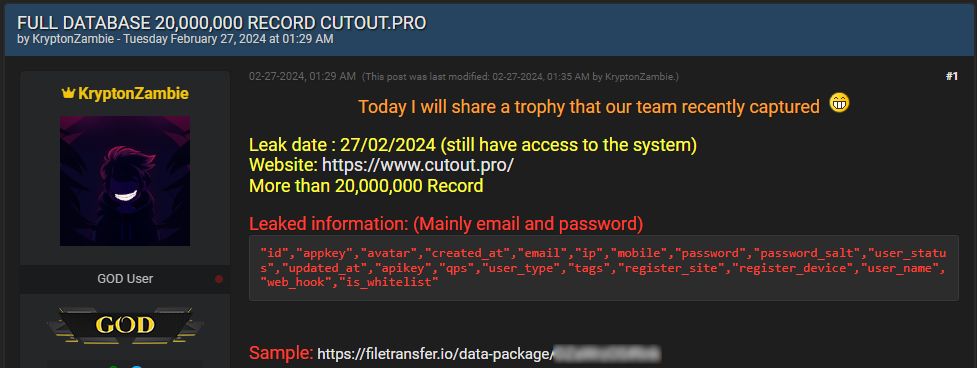
On Tuesday, somebody utilizing the alias ‘KryptonZambie’ shared a hyperlink on the BreachForums hacking discussion board to CSV information containing 5.93 GB of knowledge stolen from Cutout.Professional.
These CSV information comprise what seems to be a database dump consisting of 41.4 million information, with 20 million of these information consisting of distinctive e mail addresses.
The cybercriminal additionally acknowledged that they nonetheless had entry to the breached system, so the sufferer hadn’t realized the compromise by the point of the information publication.
Supply: BleepingComputer
From samples seen by BleepingComputer, the information that was leaked consists of the next data:
- Person ID and profile image
- API entry key
- Account creation date
- E mail deal with
- Person IP deal with
- Cell phone quantity
- Password and salt utilized in hashing
- Person sort and account standing
Data breach monitoring and alerting service Have I Been Pwned (HIBP) added the breach to its catalog yesterday, confirming that the leaked dataset consists of the knowledge for 19,972,829 individuals.
Additionally, the menace actor distributes the information on their private Telegram channel, inflicting a a lot wider circulation of the stolen knowledge.
Although Cutout.Professional has not verified the security incident from their facet by way of an official assertion, HIBP’s founder Troy Hunt advised BleepingComputer that he independently verified a number of matches from the leaked e mail addresses, confirming that password reset requests went by way of.
BleepingComputer additionally confirmed yesterday that emails listed within the knowledge leak match reliable Cutout.Professional customers.
BleepingComputer emailed the corporate at the moment and yesterday however didn’t obtain a response. Hunt says he additionally tried to contact the service supplier, with related outcomes.
If in case you have used Cutout.Professional prior to now, it is strongly recommended that you just reset your password instantly on the service and some other on-line platforms the place you could be utilizing the identical credentials.
MD5 password hashes are thought-about comparatively simple to crack by fashionable requirements, which is why safer algorithms like bcrypt have outmoded them. Therefore, menace actors brute-forcing the leaked password hashes is a practical chance.
Moreover, all Cutout.Professional customers needs to be looking out for focused phishing scams that try to assemble additional data from the consumer.




