Hackers related to China’s Ministry of State Safety (MSS) have been linked to assaults in 17 totally different international locations in Asia, Europe, and North America from 2021 to 2023.
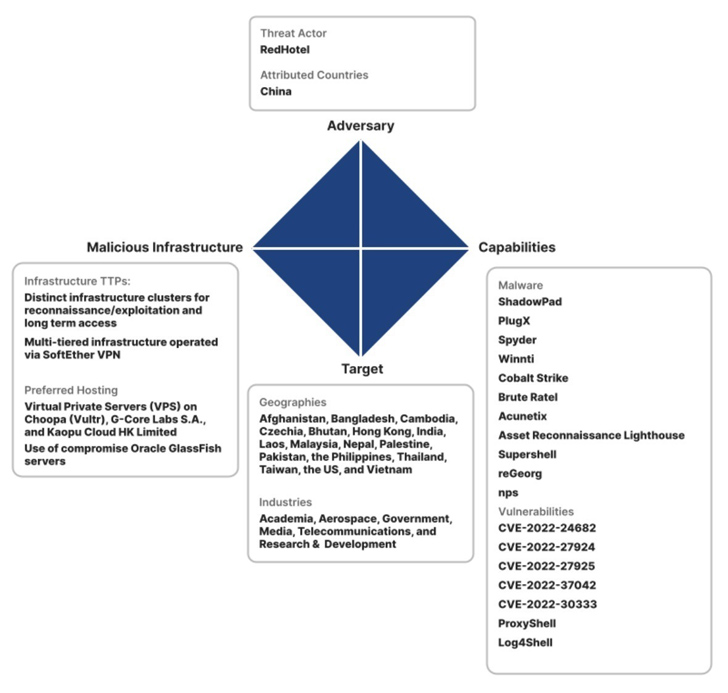
Cybersecurity agency Recorded Future attributed the intrusion set to a nation-state group it tracks beneath the title RedHotel (beforehand Menace Exercise Group-22 or TAG-22), which overlaps with a cluster of exercise broadly monitored as Aquatic Panda, Bronze College, Charcoal Hurricane, Earth Lusca, and Pink Scylla (or Pink Dev 10).
Lively since 2019, among the outstanding sectors focused by the prolific actor embody academia, aerospace, authorities, media, telecommunications, and analysis. A majority of the victims through the interval have been authorities organizations.
“RedHotel has a twin mission of intelligence gathering and financial espionage,” the cybersecurity firm mentioned, calling out its persistence, operational depth, and world attain. “It targets each authorities entities for conventional intelligence and organizations concerned in COVID-19 analysis and expertise R&D.”
Development Micro, in early January 2022, described the adversary as a “highly-skilled and harmful risk actor primarily motivated by cyber espionage and monetary acquire.”
The group has since been linked to exploitation of Log4Shell flaws in addition to assaults aimed toward telecommunications, academia, analysis and growth, and authorities organizations in Nepal, the Philippines, Taiwan, and Hong Kong to deploy backdoors for long-term entry.
Attack chains mounted by RedHotel have weaponized public-facing functions for preliminary entry, adopted by using a mixture of offensive security instruments like Cobalt Strike and Brute Ratel C4 (BRc4) and bespoke malware households comparable to FunnySwitch, ShadowPad, Spyder, and Winnti.
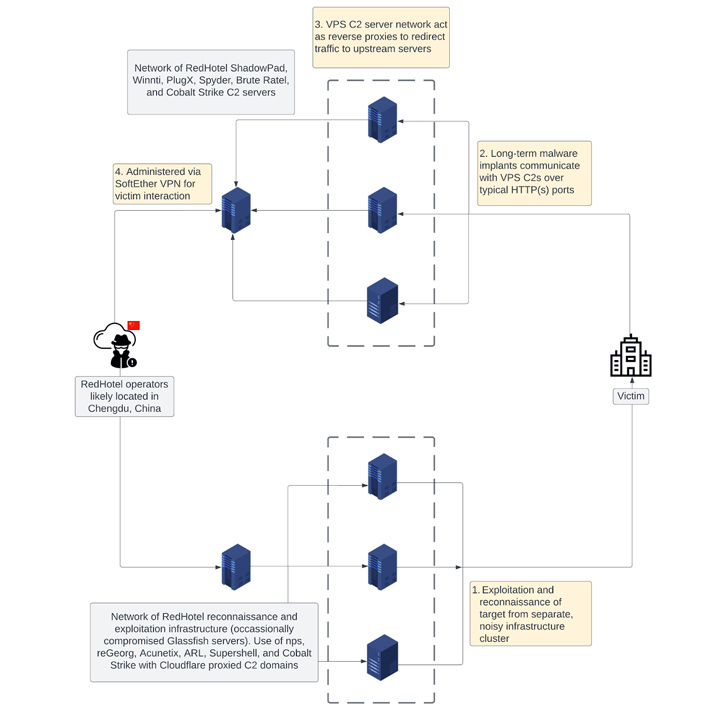
A noteworthy facet of the actor’s modus operandi is using a multi-tiered infrastructure, every specializing in preliminary reconnaissance and long-term community entry through command-and-control servers. It predominantly makes use of NameCheap for area registration.
In a single late 2022 marketing campaign, RedHotel is claimed to have leveraged a stolen code signing certificates belonging to a Taiwanese gaming firm to signal a DLL file liable for loading BRc4. The post-exploitation toolkit, for its half, is configured to speak with abused compromised Vietnamese authorities infrastructure.
“RedHotel has exemplified a relentless scope and scale of wider PRC state-sponsored cyber-espionage exercise by sustaining a excessive operational tempo and concentrating on private and non-private sector organizations globally,” Recorded Future mentioned.
The event comes because the Washington Publish reported that Chinese language hackers had “deep, persistent entry” to categorised protection networks in Japan, prompting the U.S. Nationwide Safety Company (NSA), which found the breach in late 2020, to personally report the matter to authorities officers.




